Deployment Considerations
Successful NAC deployment with Genian NAC
Establishing network access control can lead to changes in the network environment. To avoid distruption to end-users, Genian NAC uses a phased approach to deployment. Based on the experience gained by deploying NAC to many customers over 10 years, Genians highly recommends the following deployment steps:
Step 1: Gain visibility into your network assets
Understanding your network and user environment is the most important factor in establishing security policies and successfully applying network access control.
Having visibility into the network and the user device means that the following information can be monitored in real time:
- Exact type and quantity of devices in the network, including switches / routers and their configuration
- Operating system / hardware / software information of the user's device
- Wireless LAN environment
There are many ways to achieve this visibility. We hear from many customers that they have failed to achieve visibility through the 802.1x access control method, which has a high degree of implementation complexity. It is very difficult to establish gradual network access control through 802.1x, because 802.1x is a technology designed for control rather than visibility. This means that network control must be established before visibility is obtained.
Another method is switch device integration via SNMP / CLI. This makes it easier to obtain visibility without control. However, considering compatibility with switch manufacturers and models, as well as un-managed switch devices, there are still considerable limitations.
To address these complexity and compatibility issues, Genians offers a method of securing visibility through an independent Network Sensor. The network sensor is connected to each subnet (broadcast domain) and can be deployed without changing the existing network environment. Usually, installation and full visibility can be acheived in under three days.
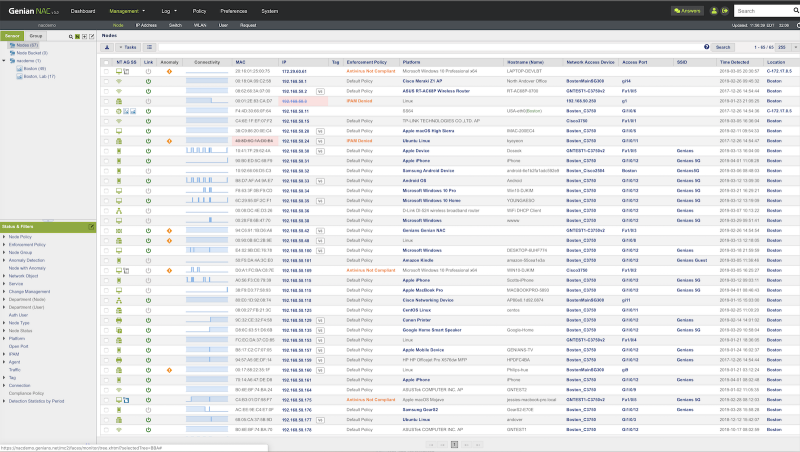
Genian NAC also provides Agent software for greater visibility into Windows and MacOS operating systems. It can be installed on the user's system to collect information (operating system / hardware / software / update, etc.) desired by the administrator.
Step 2: Classify assets and check compliance
Once the visibility of the IT assets is established, the next step is to classify known assets. Genian NAC offers more than 500 different conditions for grouping assets. Node group membership updates in real time as the status of the node changes.
Ideally, groups are defined by multiple perspectives, such as who the intended user is, what kind of device the node is,or what subnet the nodes are part of. To this end, various additional information such as manufacturer / product name / model information, connection method, and more are provided by Genian NAC's Device Platform Intelligence.
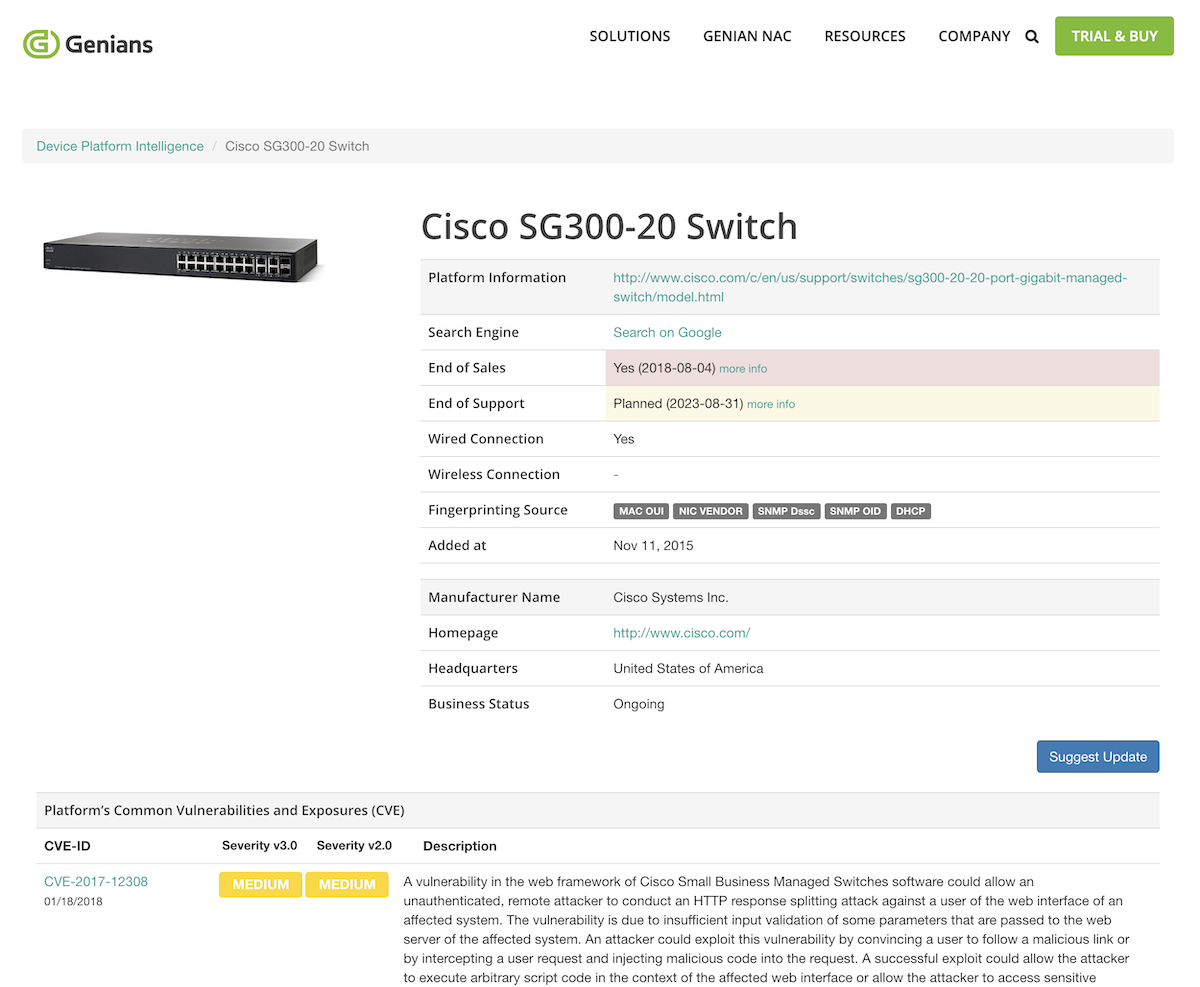
In addition to administrative classification, classification of devices that violate security regulations is also very important.
In general, groups may be configured for:
- Devices that are not assets of the company are connected to the network (personal devices)
- PC's without antivirus software
- Non-Authenticated devices
Step 3: Establish IT security policy and remediation
Once an IT security policy is established, control of the device that violates it is required. Becasue it is not easy to control all identified violation devices at once Genian NAC provides a step-by-step, automated approach.
The Agent is equipped with a variety of control action plug-ins to automatically process various security settings and configurations without user intervention. The Captive Web Portal (CWP) can also guide you through the tasks you need to perform, such as guest user on-boarding.
For more information on control actions, see Controlling Endpoints with Agent
Step 4: Enforce network access control and Quarantine non-compliance devices
After removing the known unauthorized device through the above steps and completing the necessary security measures for the user's device, the remaining task is to continuously monitor whether the security regulations are complied with, and to control network access by the devices that violate the regulations. At this stage, various control methods can be selected according to the network environment and required security level. Genian NAC provides a variety of controls for this.
- 802.1x
- Layer 2 (ARP, DHCP)
- SNMP/CLI (Port Shutdiown)
- Port Mirror (SPAN)
- Inline
- Integration with 3rd party device (Firewall, VPN, etc)
- Agent
For details about each control method, see Policy Enforcement Methods
Technical Considerations
| Topic | Layer 2 Sensor/Enforcer | SNMP/CLI | Port Mirror (SPAN) | Inline | 802.1x | Agent |
|---|---|---|---|---|---|---|
| Access Control at Layer 2 | Yes
|
Yes
|
No
|
No
|
Yes
|
No
|
| Access Control at Layer 3 | RBAC
|
Switch Port ACL
|
RBAC
|
No
|
Switch Port ACL
|
OS Firewall
|
| Post-admission Control | ARP, DHCP
|
VLAN/ACL/Shutdown
|
TCP RST, ICMP unreach.
|
Filtering
|
CoA*
|
OS Firewall
|
| Additional Hardware | Network Sensor
|
Managed Switches
|
Full traffic capable Device,
Tap Device,
SSL Decryption Device
|
Full traffic capable Device
|
802.1x Switch/AP
|
No
|
| Endpoint Dependency | No
|
No
|
No
|
No
|
802.1x Supplicant
|
Agent required
|
WLAN Security
|
Monitoring
(WNIC on Sensor)
|
Monitoring
(SNMP with Controller)
|
No
|
No
|
Monitoring / Control
(WPA2-Enterprise)
|
Monitoring / Control
(SSID Whitelist)
|
| Layer 2 Security | Detect MAC Spoofing,
Detect Rogue DHCP,
Managing IP Conflict
|
No
|
No
|
No
|
No
|
No
|
CoA*: Change of Authorization, RFC 5176 - Dynamic Authorization Extensions to RADIUS
Management Considerations
| Topic | Layer 2 Sensor/Enforcer | SNMP/CLI | Port Mirror (SPAN) | Inline | 802.1x | Agent |
|---|---|---|---|---|---|---|
| Network Config Change | Trunk port (optional)
|
Switch Config,
VLAN/ACL
|
Tap Device,
SPAN Port
|
Gateway Change
|
Switch Config,
VLAN/ACL,
Endpoint Config
|
No
|
| Compatibility Issue | No
|
Vendor-dependent
SNMP MIB/CLI
|
No
|
No
|
RADIUS Vendor Attribute,
non-802.1x capable Device
(Poor wired device support)
|
OS Type/Version
|
| Easy of Deployment | Easy
|
Difficult
|
Intermediate
|
Easy
|
Very Difficult
|
Intermediate
|
Phased Deployment
(Discover First, Control Later)
|
Yes
|
Yes
|
Yes
|
No
|
Must be controlled from
the start of deployment
|
Yes
|
| Single point of Failure | No
|
Yes
|
Yes
|
Yes
|
Yes
|
No
|
| Vendor Lock-in | No
|
Intermediate
|
No
|
No
|
High
|
Intermediate
|
| Recommended for | Essential Discovery
and Control
|
Extended information
and port control
|
Wireless network
|
Extended information
and enforce compliance
|
Deployment Models
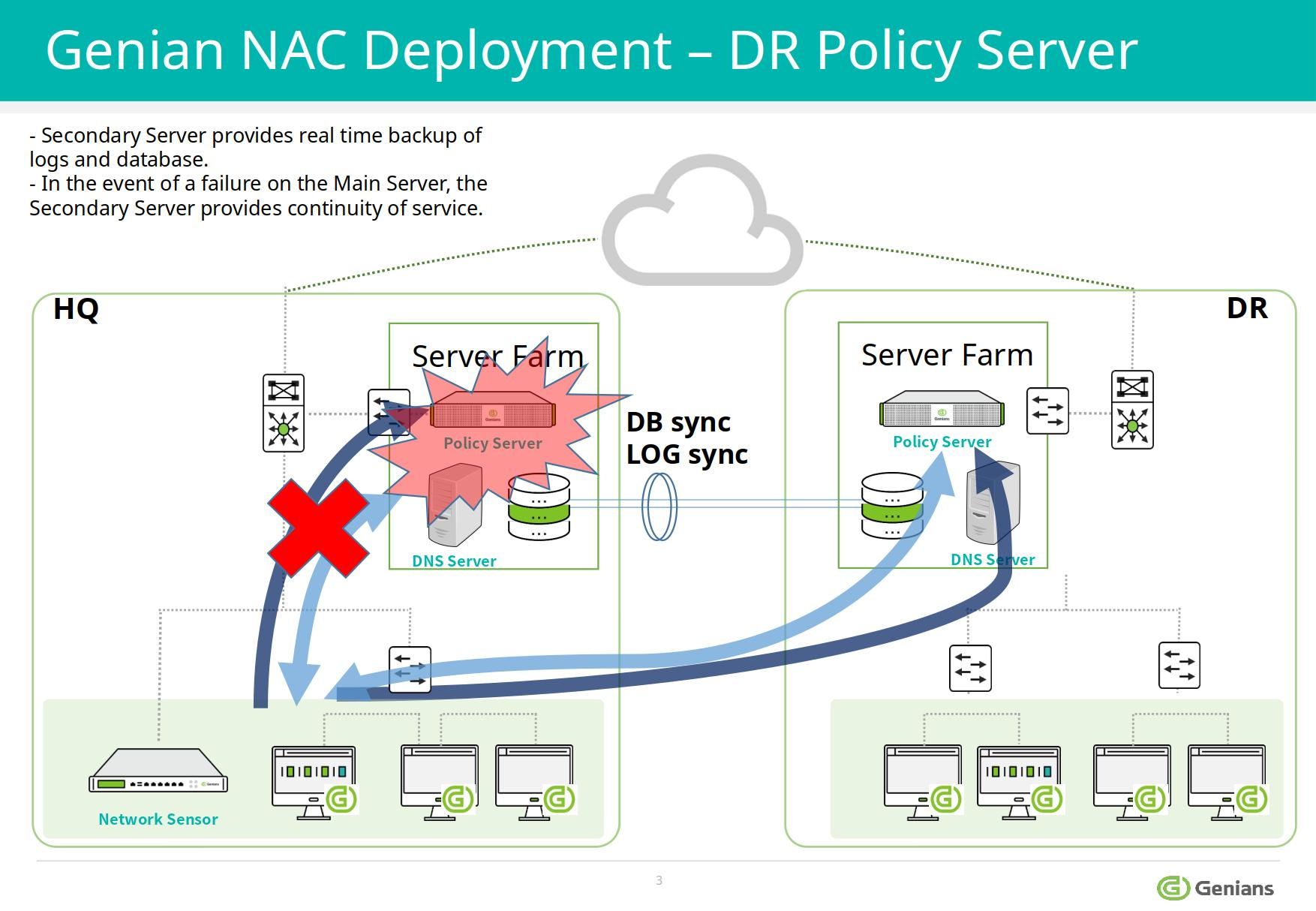
On-Premises
Policy Server and Network Sensor can be deployed flexibly.
- Policy Server/Network Sensor combined may be hosted on a single appliance or separately
- Sensor(s) may be deployed centrally (802.1Q trunk or mirror port) or distributed between networks.
- Trunked Sensors support up to 128 Vlans(recommended 64 VLANs)
- For more info on sensor modes , see: Controlling Network Access
Your Cloud
The Policy Server may be hosted in an existing Private Cloud by utilizing the publicly available AWS AMI. Deployment instructions are posted in the AWS Market Place product listing for Genian NAC Policy Server.
Genians Cloud
The Policy Server may be hosted in a Private site in the Genians Cloud which can be launched from Genians.com.
NAC AS A SERVICE (MSP READY)
Essential Features For CyberSecurity-As-A-Service
Enhance the way of monitoring your customer network:
- Security infused IT Asset Management empowered by Device Platform Intelligence
- Ongoing Compliance-As-A-Service for Networks and Endpoints
- Network anomaly detection
- Customizable dashboards and reports
Secure network connections made by any type of IP enabled devices at the edge:
- Control unauthorized/rogue/misconfigured devices
- Support a productive onboarding process
- Quarantine/Remediation
- Desktop configuration management
Plus, the built-in services:
- RADIUS Server for AAA (802.1x)
- DHCP Server for IP management
- Syslog Server for Log and Event Management
Cloud Ready
Supports various Cloud environments:
- Public Cloud (AWS, Azure, Google)
- Private Cloud (VMWare, OpenStack)
- Nutanix Hyperconverged Infrastructure (HCI)
- Policy Server: Supports multi-tenancy (Docker container)
- Network Sensor: Support Universal customer premises equipment (uCPE)
- Agent: Multi functional features and customization
Management:
- One-stop service (sites, users, licenses, subscriptions, billing)
- Virtual domain support
- Centralized dashboard/reports
- Zero Config Provisioning
- White label service