Integrating Palo Alto Networks Firewall
This guide provides an overview of integration with Palo Alto firewall. It includes the following information:
1. About this Guide
This guide describes how Genian NAC engineers and enterprise operators can send information of user authentication to PAN firewall.
PAN Firewall generally requires that when a user changes a department or location, the IP information changes and the assigned permissions are modified accordingly. IP-based firewall policies do not know who is using an IP, but they can work with Genian NAC to get user information about an IP.
Based on this information, even if the user's department or location is moved and the IP information is changed, the user will be able to apply the authority assigned to each user without modifying the rule in the firewall. This efficiently improves administrator's internal infrastructure operation and security.
For more info about PAN firewalls , see https://docs.paloaltonetworks.com/pan-os
2. Deployment of Genian NAC using PAN Firewall
Genian NAC provides the integration of authentication. The PAN firewall refers to the IP and user authentication information provided by Genian NAC, and performs USER-ID mapping to enable access control by user role in the PAN Firewall.
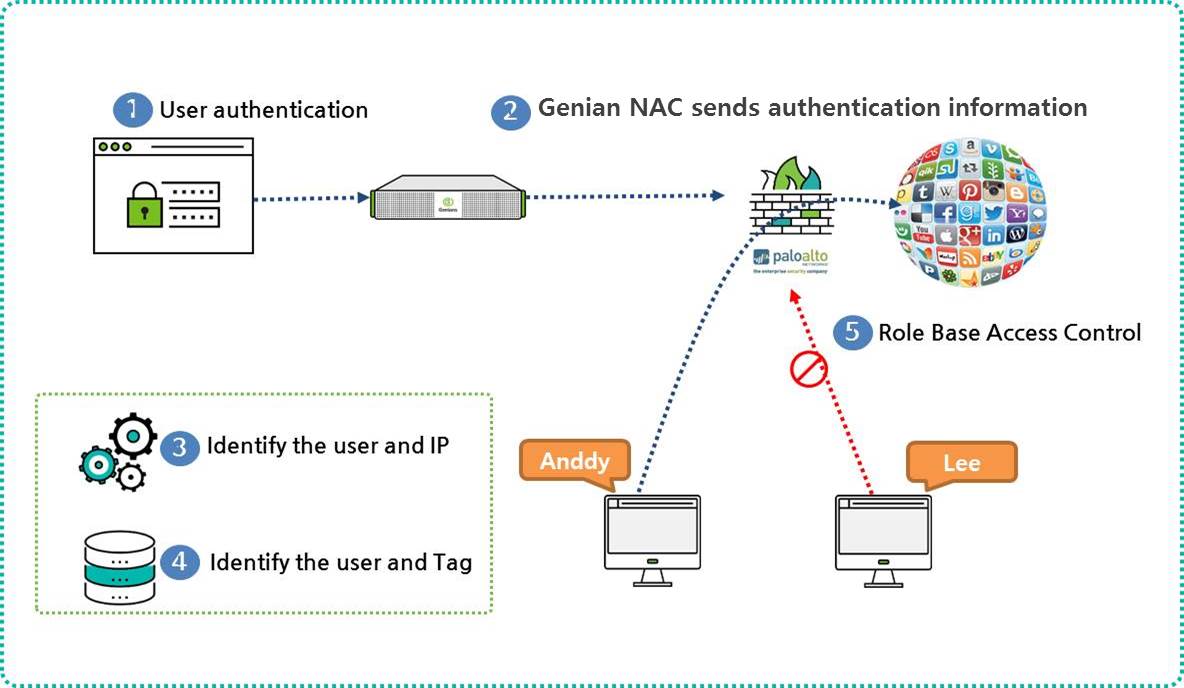
The authentication process is described below:
- User Authentication in Genian NAC
- Genian NAC sends authentication user and IP information to PAN firewall
- The PAN firewall compares the authentication user and IP information it receives from Genian NAC with its own user ID table.
- PAN confirms tag assigned to User-ID
- Establish role-specific access Enforcement Policy based on tag assigned to each user
3. Configuring PAN Firewall for integration via XML API
3.1 Create an Admin role on the PAN firewall. - Go to Device > Admin Roles > Add - Create the role Name Genian_NAC_SSO, under the XML API tab - Enable everything and validate it with OK
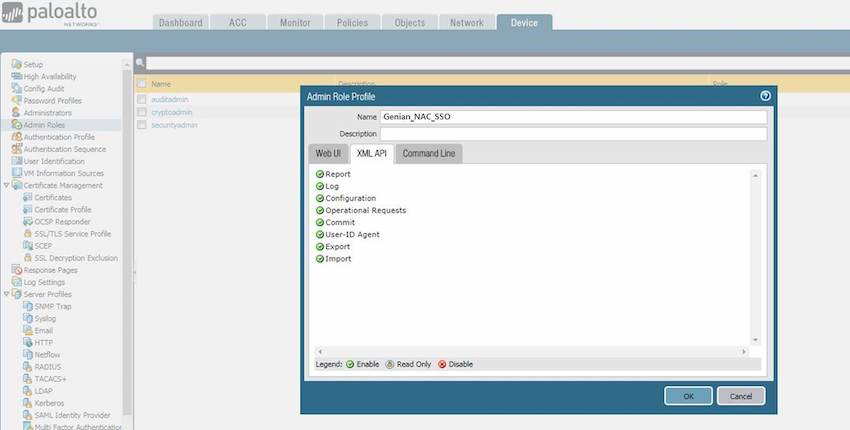
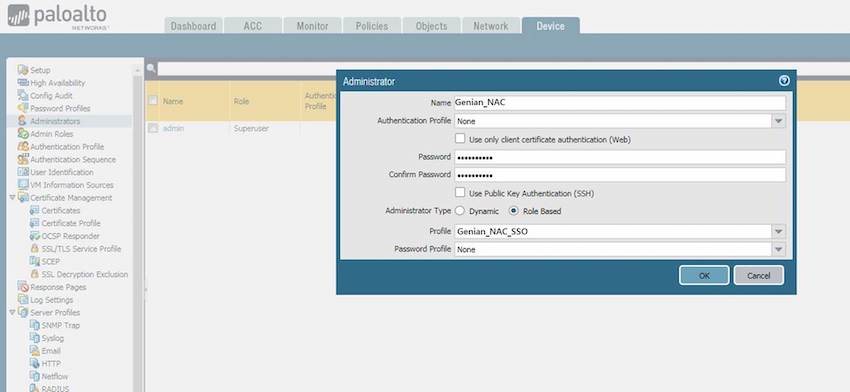
3.2 Create an account for Genian NAC. Assign the SSO role to the account. - Enter a Name: Genian_NAC - Select the Administrator Type: Role Based - Select the Profile: Genian_NAC_SSO
3.3 Generate the XML Key. Go on this URL: https://[ IP of PAN firewall]/api/?type=keygen&user=[username]&password=[password] You can see the generated Key below:
**Script**
<response status = 'success'>
<result>
<key>LUFRPT1KbW80SU1hRXJuNk5XNHBudUhCNGMydE0rSUk9RFIzdEJ5RGcwWkRCVlhYMXl0Q1FPdz09
</key>
</result>
</response>
3.4 Configure the Genian NAC for sending SYSLOG. Genian NAC uses filters in the audit log to integrate with XML.
- Go to Log in the top panel
- Go to Log > Search > Advanced Search > Log ID > Check Authentication > Click Search button in the left Log panel
- You will see the Log of Authentication user and then you click the “save as” button
Enter a Name: SSO_PaloAlto Set the Webhook URL:
Call the PAN firewall XML
https://[IP of PAN firewall]/api/?type=user-id&action=set&key=LUFRPT1KbW80SU1hRXJuNk5XNHBudUhCNGMydE0rSUk9RFIzdEJ5RGcwWkRCVlhYMXl0Q1FPdz09
Select a character Set: EUC-KR Select a Method: POST Enter the POST Data:
Script
<uid-message>
<version>1.0</version>
<type>update</type>
<payload>
<login>
<entry name="{ID}" ip="{_IP}" timeout="20" />
</login>
</payload>
</uid-message>
Select a Content-Type: multipart/form-data
3.5 Configuring User Identification on Security Zones. PAN firewall policy rules use security zones to identify the Data traffic which flows freely within the zone, not flowing freely between the different zones until you define the allowed security policy rules. To enable enforcement of user identity, you must enable user identification in both the inbound and outbound zones that are passed by end-user traffic.
To enable User Identification - Go to Network > Zone - Select Enable User Identification and click OK
3.6 Verify that the firewall is successfully receiving login events from SSH and Web Console.
CLI Command
admin@PA-VM> show user ip-user-mapping all
IP Vsys From User IdleTimeout(s) MaxTimeout(s)
--------------- ------ ------- --------- -------------- -------------
172.29.101.1 vsys1 XMLAPI genian 1111 1111
Total: 1 users
WebConsole - Go to Monitor - Go to Logs > User-ID in the left Monitor panel - You will see the list of authentication via Genian NAC
4. Configuring PAN Firewall for Integration via SYSLOG
4.1 Create a filter. The Palo Alto Firewall creates a log filter to distinguish authentication-related messages when receiving Syslog messages from Genian NAC.
- Go to Device on the top panel
- Go to User Identification > User Mapping > Click the Button look like Gear on PAN firewall User-ID Agent Setup Tab
- Go to Syslog Filters > Add
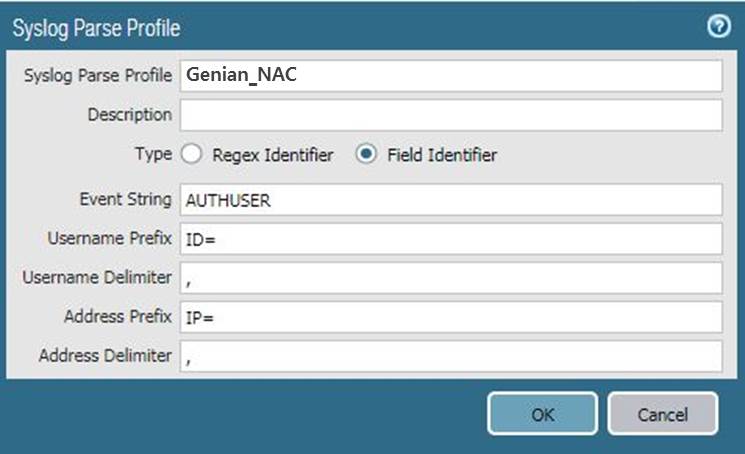
Enter values
Enter a Syslog Parse Profile: Genian_NAC
Enter a Event String: AUTHUSER
Enter a Username Prefix: ID=
Enter a Username Delimiter: ,
Enter a Address Prefix: IP=
Enter a Address Delimiter: ,
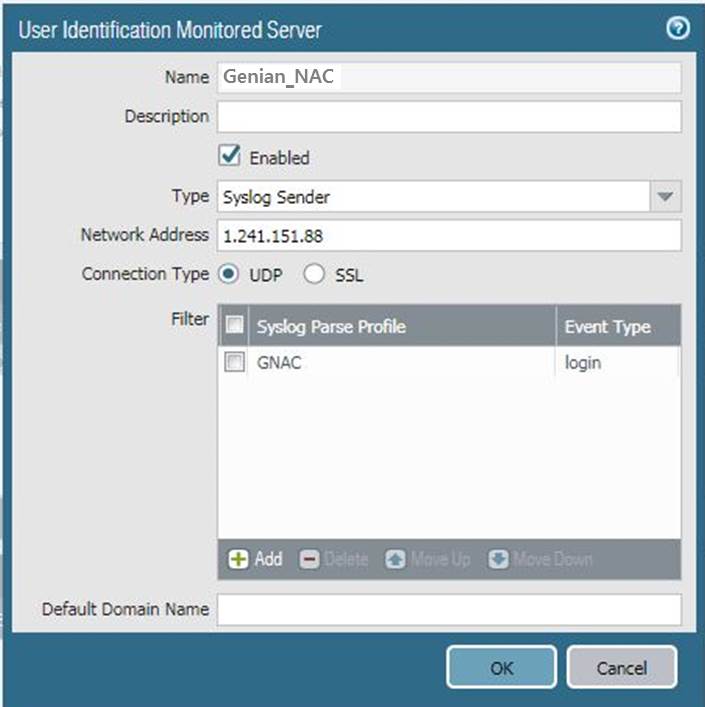
4.2 Specify the SYSLOG sender that the PAN firewall monitor.
- Go to Device > User Identification > User Mapping and ADD an entry to the Server Monitoring list
Enter values
Enter a Name to identify the sender
Make sure the sender Profile is Enabled (default is enabled)
Set the Type to Syslog Sender.
Enter the Network Address of the Genian NAC IP address
Select SSL(default) or UDP as the Connection Type
Note
The UDP protocol is unencrypted data. It is recommended to use of the SSL protocol.
The listening ports(514 for UDP and 6514 for SSL)
4.3 Enable SYSLOG listener services. It is able to listen to the SYSLOG from Genian NAC.
- Go to Network > Network Profiles > Interface Mgmt > ADD a new profile
Enter values
Enter a Name to identify the Network Profile: Allow Genian NAC
Check the User-ID SYSLOG Listener-SSL or User-ID SYSLOG Listener-UDP
Click OK to save the interface management profile
4.4 Assign the interface Management profile to the interface.
- Go to Network > Interfaces and edit the interface
- Go to Advanced > other info > select the Interface Management Profile > select the Allow Genian NAC > Click Ok
- Commit
4.5 Configure the Genian NAC for sending SYSLOG. Genian NAC uses filters in the audit log to integrate with SYSLOG.
- Go to Log in the top panel
- Go to Log > Search > Advanced Search > Log ID > Check Authentication > Click Search button in the left Log panel
- You will see the Log of Authentication user and then you click the “save as” button
Enter values
Enter a Name
Enter a Server IP address[ Palo Alto IP]
Select the Protocol either UDP or TCP(TLS)
Set a Server port(UDP for 514, TCP(TLS) for 6514)
Enter the SYSLOG Message: USERAUTH, ID={ID}, IP={_IP}
Click the Save
4.5 Verify that the user mappings when users log in and out.
CLI command
admin@PA-VM> show user ip-user-mapping all type SYSLOG
IP Vsys From User IdleTimeout(s) MaxTimeout(s)
--------------- ----- ------- -------------------- -------------- -------------
172.29.101.1 vsys1 SYSLOGI genian 2220 2220
Total: 1 users