Understanding Genian Insights E
What is EDR
The problems EDR solves
Gartner announced one of its strategic technologies is an Adaptive Security Architecture that can be quickly adapted to a changing environment.
The EDR solution can satisfy the detection and response areas of the adaptive security architecture.
Genian Insights E can work with Genian NAC to efficiently respond to threats.
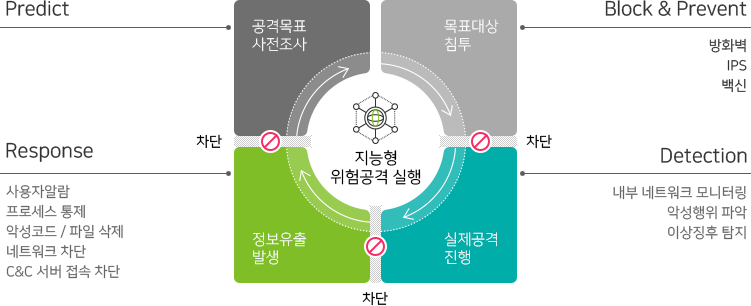
Prevention
Authentication/identification of terminals and users is carried out through Genian NAC, and the status of required S/W installation and security patch application is continuously monitored to isolate unpatched terminals from the network.
Investigation / Analysis(Detection)
By installing an agent and log interlocking with Genian NAC, the main actions occurring in the terminal are monitored, stored in real time, and then analyzed.
Proliferation/Recurrence Prevention (Response)
Features of Genian Insights E
Genian Insights E (Genian Insights E) is a terminal-based intelligent Threats Threat Detection & Response (EDR: Endpoint Detection & Response) that can quickly detect, respond, and analyze various types of malicious codes and abnormal behaviors occurring in the terminal. Response) solution.
Rapid Threat Detection & Response is possible through the latest indicators of compromise (IOC: Indicators of Compromise) in the execution stage of security attacks such as APT and ransomware, which cannot be fundamentally defended by identifying malicious behaviors on internal networks and devices and detecting abnormal signs do.
Utilization of the latest IOC suitable for the domestic environment
- Response to the latest threats and incidents with periodic IOC updates
- Provides information on the level of risk, reliability and type of detected threats
- IOC DB System considering the domestic environment (minimize false positives and false positives)
- Addition of Custom Malware Hashes/IP, Good Hash/IP and System function
Various detection modules provided
- IOC (Indicator Of Compromise) violation indicator
- ML (Machine Learning) Machine Learning: Response to unknown similar variants
- UEBA (User & Entity Behavior Analytics) User Behavior Analysis
- YARA Rule
Ecosystem linkage
- Share false positives and latest Threat Analysis results (reputation service) through the Ecosystem
- Process and redistribute collected Threats and Exceptional data
Analysis information visualization
- Provides 16 types of flexible widgets that enable data visualization in addition to basic information required by security users (Users can be added)
- System/infected terminal/risk-abnormal terminal/process/access information/newly created file monitoring possible
- Various Dashboard Settings such as System status / NAC sensor status / Genian product status are available (Import and Export supported)
- Threats list and Analysis screen provided
Light Agent
- Agent information collection design to minimize terminal load (using about 25MB resources)
- Data analysis is performed on Genian Insights E server
Easy to apply and expand
- Install NAC plug-in based extension module
- Design that can be quickly applied throughout the company when additional function modules are introduced