Threat detection technology
Genian Insights E detects and responds to Threats using various detection modules according to Threats type.
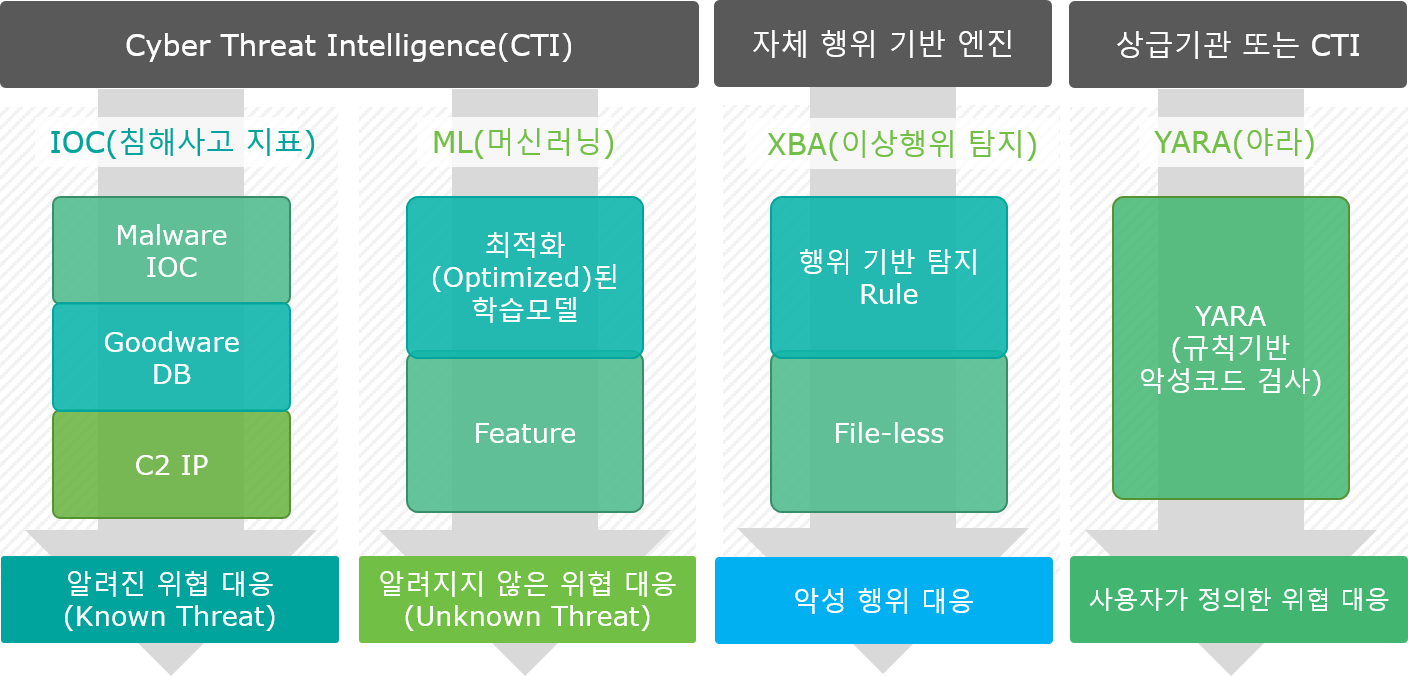
File-based Threats are largely classified into Malware, and malicious code can be subdivided into Known Threats and Unknown Threats.
File-less-based Threats are classified as Anomaly and are detected by the behavior-based anomaly detection engine.
This chapter describes various Threats detection techniques.
Malware detection
IOC (Indicator of Compromise) collects traces of infringement incidents that occur and are recorded around the world and systems this information into a separate DB,
The Insights Policy server periodically communicates with the external IOC DB server to update the latest threat information.
In a closed network environment, you can directly update the IOC DB on a monthly basis in the policy server.
When an event for a file or process occurs in Endpoints, the Threat Detector engine of the Policy Server checks whether the hash value of the file is registered in the IOC DB.
If file information is registered, the file is classified as Known Threats, and you can check the reliability, risk, and malware type information registered in the IOC.
If the file information is not registered in the IOC DB, check the machine learning information.
machine learning detection
If the type of file among the information collected by Endpoints is an executable file (PE), the feature of the file is extracted.
This feature information is used for malware detection by machine learning.
If the file is viewed, it is classified as Known Threats, and if there is no information, it is classified as Unknown Threats.
Known Threats and Unknown Threats are alarms, process kills, and file deletions on the agent according to the policy (action method) set in advance by the user.
If it is not detected even by machine learning, it performs the procedure of once again checking whether the file is registered in an external intelligence (CTI: Cyber Threat Intelligence Service) such as Reversing Labs or VirusTotal.
Abnormal behavior detection
File-less-based threats are classified as abnormal behavior and are detected by the anomaly detection (XBA:X Behavior Analysis) engine.
The behavior-based anomaly detection engine has a predefined anomaly policy, and when anomaly is detected in Endpoints, Threat Detection & Response is possible immediately.
MITER ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge - a knowledge base that provides tactics, techniques, and procedures from an attacker's perspective as a framework) provides attack technique detection and related information.
Yara Rules detection
YARA is a tool that allows you to search and classify malicious code based on a string or binary pattern (Hex string).
In addition to finding the signature of a file using only string and binary patterns, specify a specific Entry Point value, or suggest File Offset and Virtual Memory Address.
Efficient pattern matching is possible using regular expressions.
Genian Insights E allows users to quickly and efficiently detect Threats from Endpoints through Yara Rules written by users.