Policy Enforcement Methods
You need a way to control devices that violate network policies defined by your organization. Genian NAC 6.0 provides multiple layers of enforcement methods from Layer 2 network control to agent-based. Depending on your network environment or security requirements, you can leverage the following options:
ARP Enforcement
Controlling network access according to the status of devices in the internal network has always been a challenge. Setting ACLs on routers to control access between internal networks can provide only a simple access control.
ACLs can be difficult to enforce in a DHCP environment where devices move frequently or devices that use IP change frequently. Moreover, access control between multiple devices connected to the same sub-net is the most challenging task and there are not many solutions.
A possible choice is to apply the Port based Access Control function using 802.1x to the switch port to which the device is connected. However, 802.1x can be expensive, requiring large network configuration changes, such as replacing unsupported devices and converting to a single vendor for networking equipment.
In addition, because all network devices do not support 802.1x, manual configuration is frequently required for each switch port. In an enormous enterprise network, setting an exception list for 802.1x for each switch port is complicated and time consuming.
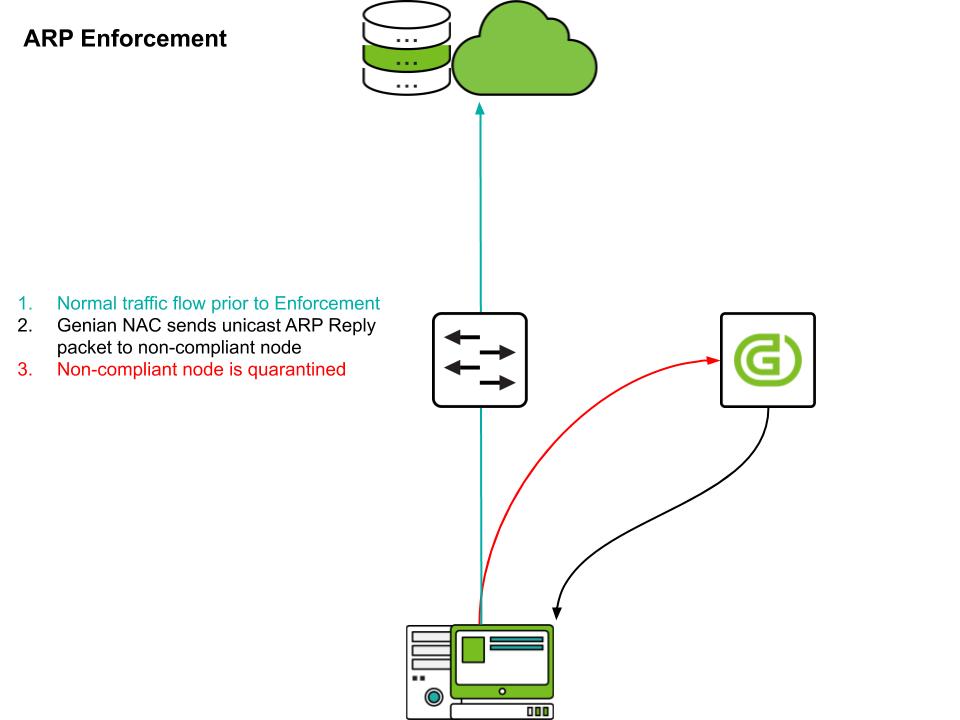
Another option is to use network access control with ARP Enforcement. ARP Enforcement uses the characteristics of the ARP protocol to perform access control. The device conducting the enforcement impersonates other network endpoints in order to intercept traffic.
Genian NAC 6.0 performs ARP Enforcement using the following procedure.
The device to be blocked generates an ARP request.
The network sensor responds to the request with its own MAC.
The device to be blocked transmits the packet to the network sensor.
The network sensor drops according to the access control policy or delivers it to the actual destination.
If the target device attempts to bypass this enforcement by setting static ARP, a bidirectional enforcement function is provided to control the reply packet generated from the communication target such as gateway, and static ARP setting can be blocked through Agent.
Genian NAC 6.0 has a built-in RADIUS server for 802.1x and ARP Enforcement via network sensor, so users can select the option best for their network environment.
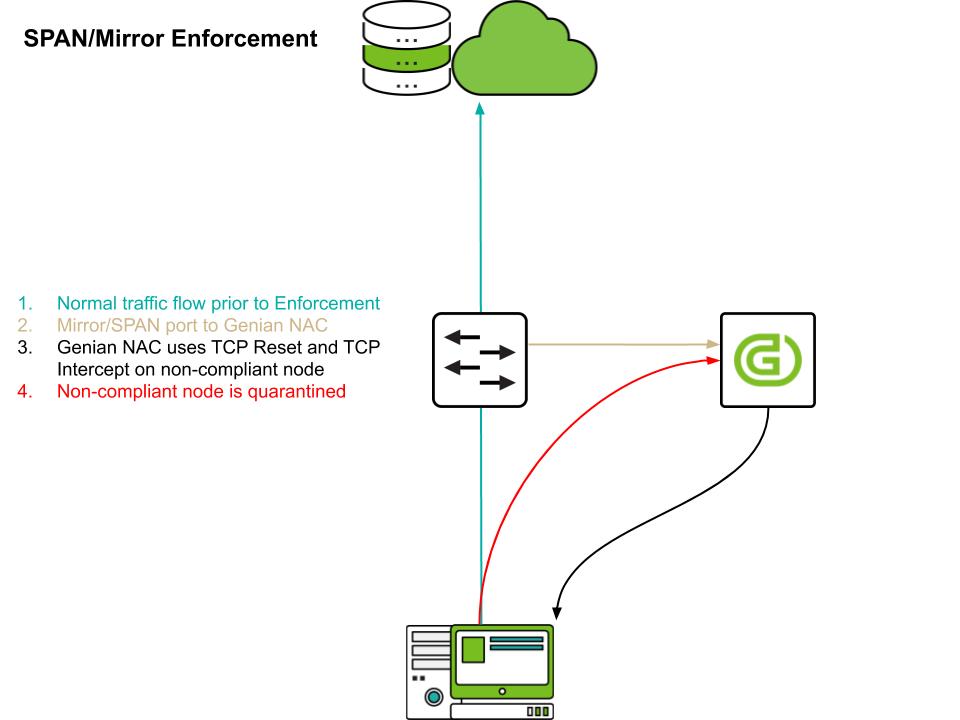
Port Mirroring (SPAN)
Genian NAC 6.0 uses Port Mirroring (SPAN in Cisco) as a way to provide access control with minimal network configuration changes. It monitors newly connected sessions through Mirroring port and blocks connection by transmitting TCP RST or ICMP Destination Unreachable packet.
To do this, you need to transfer the traffic to Genian NAC 6.0 using a Port Mirroring supported switch or a Network TAP device.
Genian NAC 6.0 offers two types of port mirroring modes.
Global Mirror Sensor
The Global Mirror Sensor can perform information collection and access control. In general, it is located in the boundary network connected to the Internet, and access control is performed while monitoring all the internal traffic.
In this setup, is recommended to use a separate network sensor with high performance hardware because it controls all nodes while monitoring all traffic generated in the network.
Local Mirror Sensor
Unlike the Global mirror, the local mirror sensor can only control packets passing through a specific network segment at that location. To solve this problem, it is possible to add a mirroring port to the network sensor installed in each end network. This makes it possible to control connections occurring within the local network.
Since the local mirror sensor is only monitoring and controlling one network segment, it can be operated in the hardware of relatively low specification as compared with the global mirror sensor.
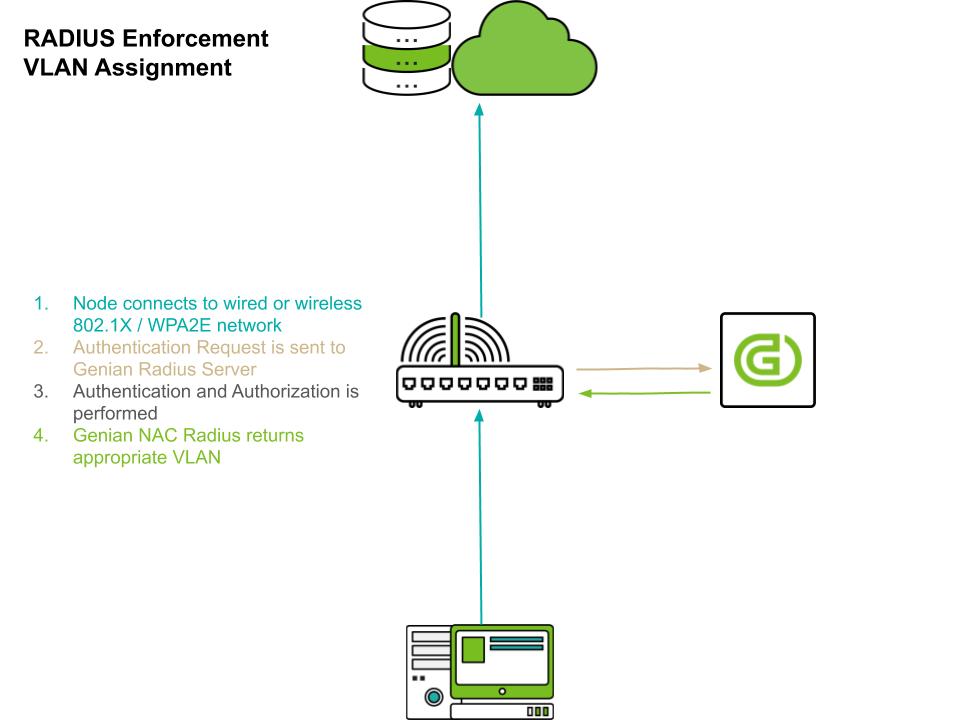
802.1x (RADIUS)
802.1x port based access control is the most ideal access control method that can be applied in enterprise wireless LAN environment. User-based authentication allows only authorized users to access the network. Also, depending on the compliance status of the device, it is possible to connect to a specific VLAN or forcibly release a connected connection.
This requires a user device that supports 802.1x, a network access device such as an 802.1x-capable access point or switch, and a RADIUS server. Genian NAC 6.0 provides a built-in RADIUS server and provides the following access control functions.
User Authentication
802.1x allows access to the network through user-based authentication instead of a weak authentication method such as a shared secret. For more information about User Authentication, see Configuring RADIUS Enforcement
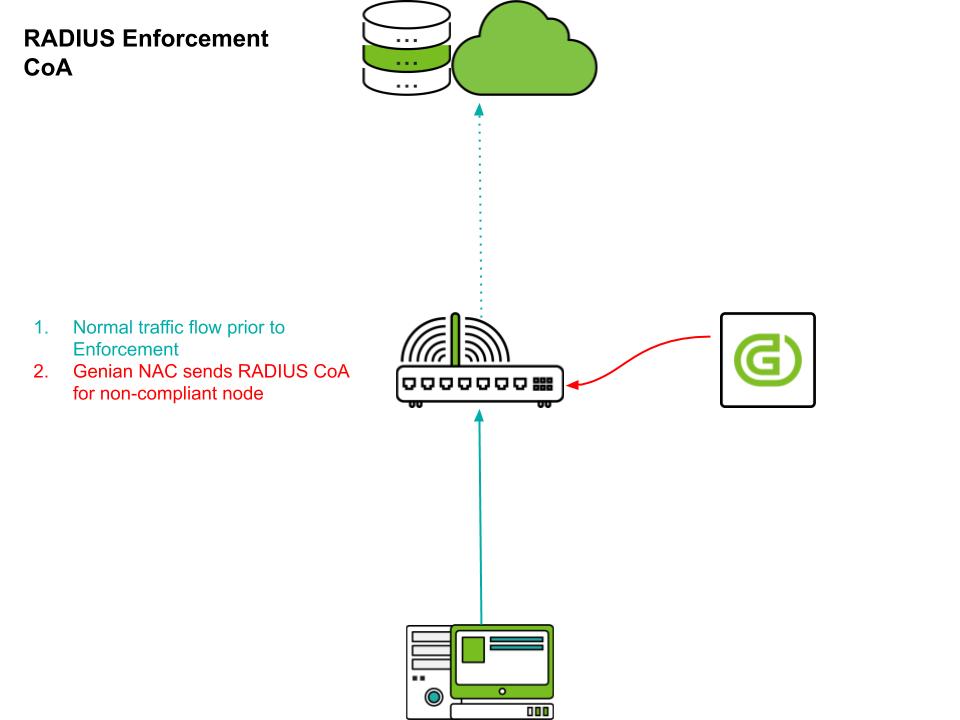
VLAN Assignment & Reassignment
Devices can be assigned to a VLAN upon connection based on Radius attributes (Standard or Vendor-specific.) If network access needs to be restricted due to device state changes, the device can be terminated using a RADIUS CoA (Change of Authorization). The disconnected device will try a new connection and connect to the isolated VLAN at this time to securely isolate the device from the network. To do this, the access point or switch must support the RFC 5176 - Dynamic Authorization Extensions to RADIUS standard.
DHCP
Genian NAC 6.0 can allocate or not allocate IP according to IP / MAC policy through built-in DHCP server. This prevents unauthorized devices from accessing the network or assigns a fixed IP address to devices with a specific MAC address.
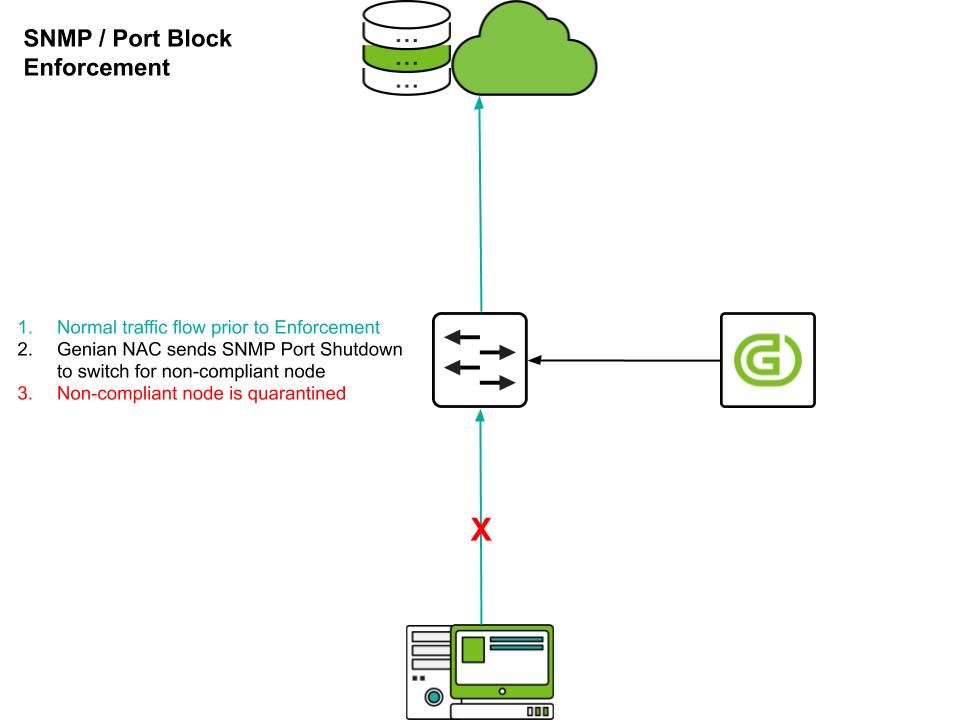
Switch Port Block
If you use a switch that supports SNMP, Genian NAC 6.0 will collect SNMP and switch and port information connected to each node. This information can be used to shut down the switch port according to the security policy of the device. Switch port block is done via SNMP Write. The switch MUST provide a writable SNMP MIB-2 ifAdminStatus property.
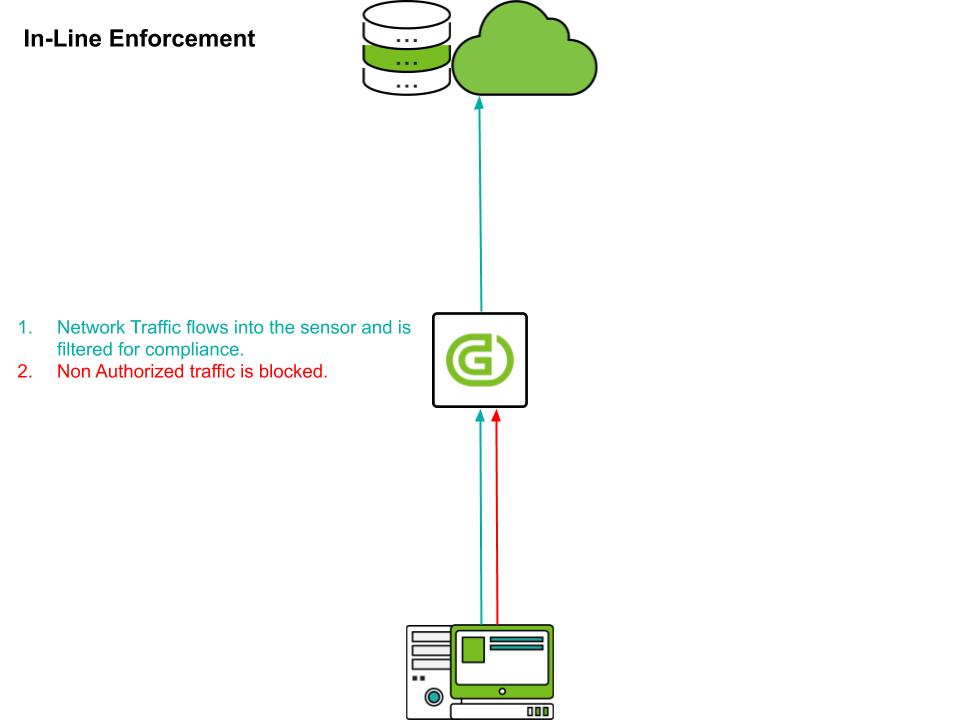
Inline packet filtering
To apply the access control policy determined by the enforcement policy, you can use a dual-homed packet filtering device between the two networks. This works the same way as a firewall. Two network interfaces operate as gateways in each network, and in the process of forwarding packets, it checks the policy and drops unauthorized packets.
Unlike the out-of-band method such as ARP or Port Mirroring method, it provides higher security because it checks the security policy against all packets passing through and transfers only allowed packets. However, this inline device is subject to security policy checks on every packet it passes through, which can cause packet transmission delays. In addition, access control policies can not be applied to packets that do not pass through this inline device. Therefore, you need to be careful about where you will install it before deployment.
For inline packet filtering, network sensor software must be installed on hardware that has two or more network interfaces. When the sensor operation mode is set to 'inline' through the setting, the security policy is applied to the received packet and then forwarded to another interface in the system according to the routing table.
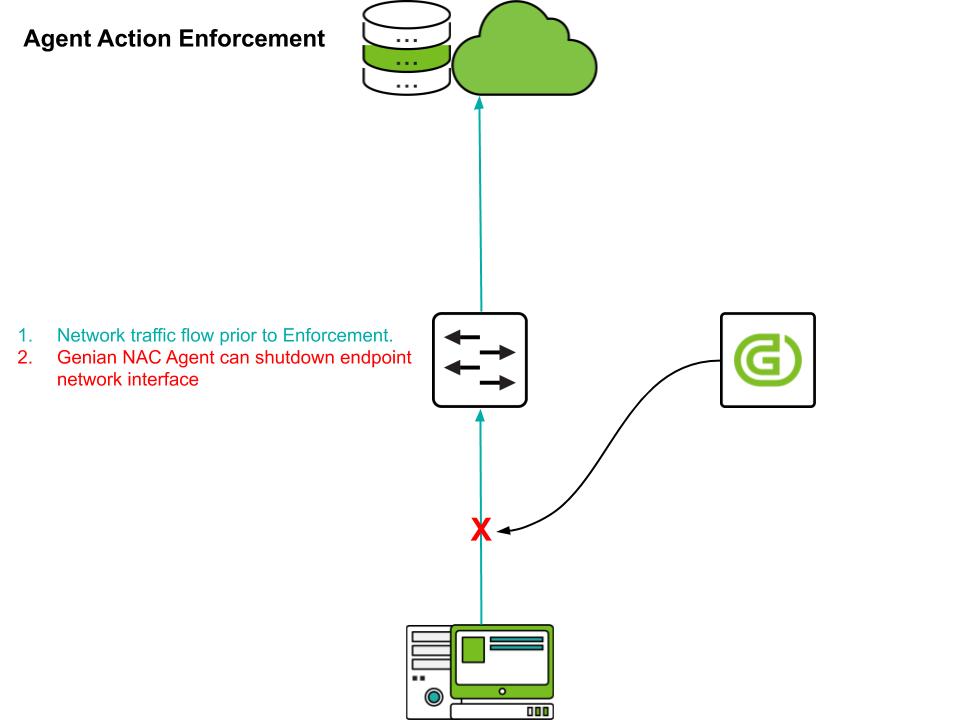
Agent Action
Depending the node policy, and enforcement policy, applied, the following agent actons can be used to control an endpoint:
Note
If you use wired/wireless network interface control to control your device, you might not be able to communicate with the policy server and receive a new policy assignment.