Blocking Unauthorized or Non-Compliant VPN Devices
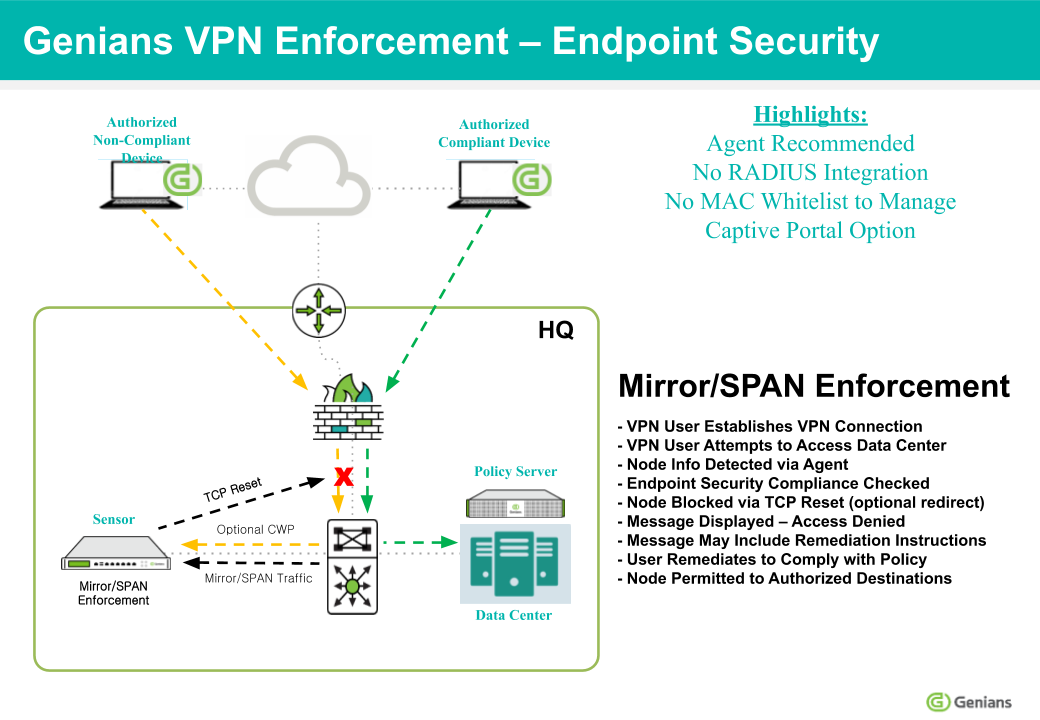
In some situations, correct user credentials may be supplied to log into a VPN, but the device itself is not approved for use on the network. This may be the result of stolen credentials,being used to access the network, or an authorized user signing into the network with an unapproved or non-compliant device. Genian NAC 6.0 can block these unapproved devices at Layer 3 using a Network Sensor deployed in Mirror Mode.
Configure Sensor
To configure a Sensor in Mirror Mode, see: Configuring Mirror Mode
Configure Groups and Enforcement Policies
Enforcing against VPN users with a mirror sensor uses the same configurations that are used for ARP Enforcement in a LAN environment.
Simply create Groups and Enforcement Policies to defined which nodes, devices, or users can access which network resources and at which times. It is also possible to redirect the non-compliant node to a captive portal, where they can be served with a message from the administer, or required to download an agent. You can create separate Groups and Policies for VPN users
The Mirror Sensor will use TCP Reset or ICMP unreachable replies to block any attempted access to prohibited resources. the VPN connection itself will remain unaltered.
To Create Groups and Enforcement Policies to allow or disallow access, see:
Note
Traffic detected by a Mirror Sensor does not result in the creation of a node in the Web Console. Therefore traffic may be blocked without any logging occurring. Nodes with an Agent installed will be shown in the Web Console, and logging will occur when their policy status changes. Use of the Agent and is recommended for gathering endpoint information.
For more content relating to VPN users, see: