Authenticating VPN Users
Genians RADIUS Server can be used as the Authentication Server for your VPN environment. You can also limit which users can authenticate with the RADIUS Server.

Integrating the Radius Server
First, ensure that the RADIUS Server is properly configured, and that your settings are compatible with your VPN environment.
See: Configuring RADIUS Enforcement
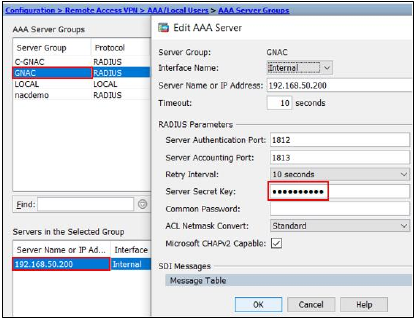
Next, configure Genian NAC 6.0 as an Authentication Server in your VPN settings, by entering the Shared Secret, Server Address, Authentication Port, Accounting Port, and other info, as shown in the example below:
Configuring Authentication Restrictions
In some situations, you may wish to place restrictions on who can authenticate using the RADIUS Server. This can be accomplished by configuring an RADIUS Policy, and setting the Access Policy to REJECT.
Go to Policy in the top panel.
Go to Policy > RADIUS Policy in the left panel.
Click Tasks > Create
For General, input Name, Priority, and activation Status.
For Conditions, select Attribute.
Select Operator and Value.
Click Add button.
For Policy, choose to REJECT Authentication Requests that match the attribute conditions.
Click Add button.
Click Create button.
When an Authentication request meets the conditions defined, it will be rejected, unless it also meets the conditions of a policy with a higher priority.