Managing Logs and Events
The Policy Server generates logs for security management purposes based on information and events collected from agents, network sensors, and 3rd party systems.
These logs are records of events occurring during device operation (e.g., device failures, illegal access attempts, policy changes, task execution results) along with their timestamps.
Administrators can quickly respond to emergency situations through logs, and efficiently establish policies by understanding node patterns through log searches.
These logs can be sent to external solutions such as SIEM solutions.
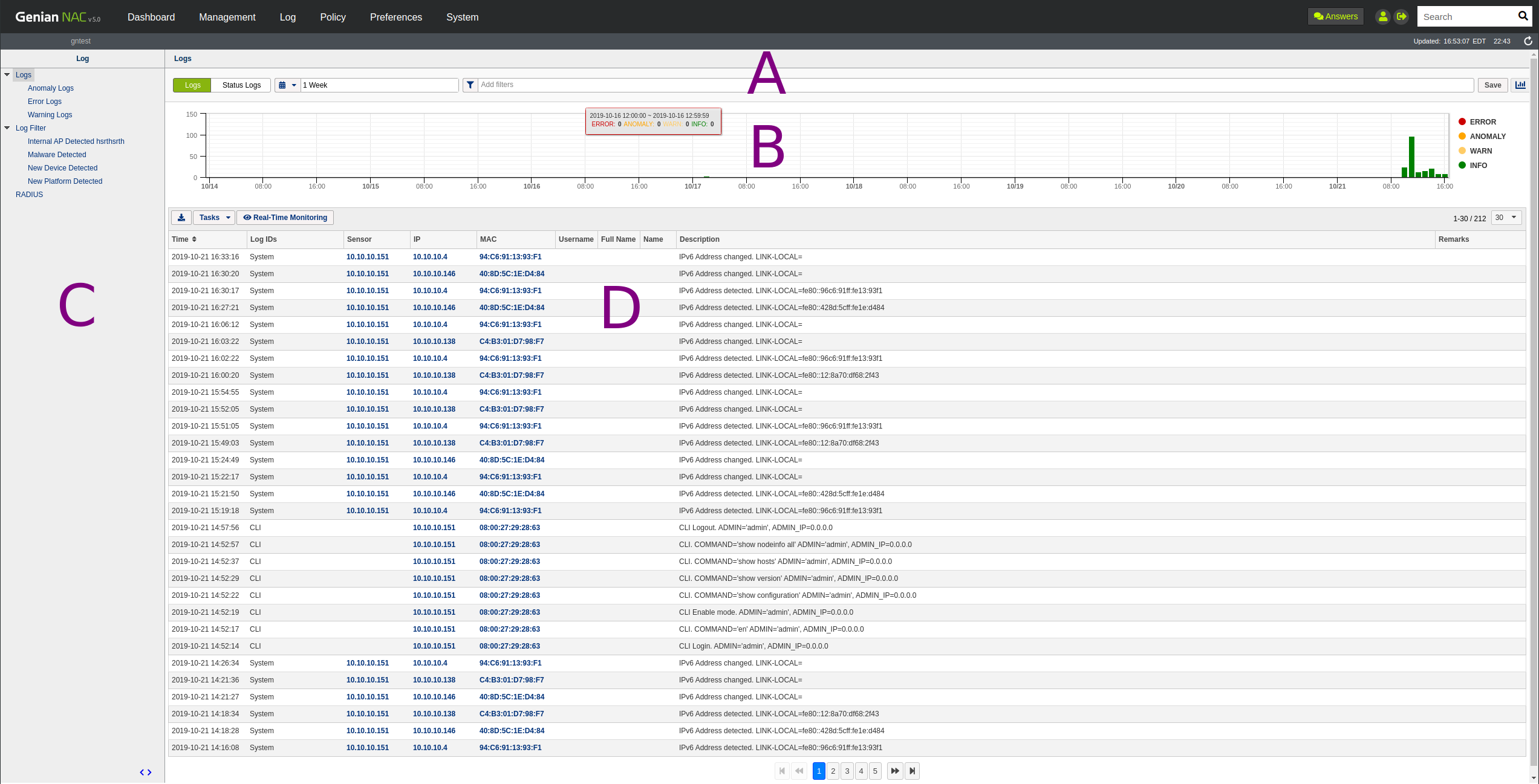
Log view consists of four main sections.
- Panel A: Status and Filter.
- Window B: Time Graph and Chart.
- Panel C: Predefined Logs that are grouped by severity, or popular use cases.
- Window D: Result window of your searching and filtering.
Log display and generation options may be configured under General > Log in the Preferences section.