CWP Page Redirection Not Occurring for Blocked Endpoints
Genian NAC displays security policies that users must comply with via CWP when a user, who has not complied with the company's security policies, attempts network access through a browser. To display the access authentication page to users, Genian NAC monitors the network communication process of the user's PC, allowing the user to see Genian NAC's CWP page instead of the page they intended to access.
Sometimes, the PC controlled by Genian NAC is not connected to the CWP page, or the web browser only displays the message "Your connection is not private."
This issue occurs when a user not complying with security policies attempts to connect to a specific site using HTTPS service. Genian NAC fundamentally bypasses packets originating from the endpoint to display the CWP screen to the user, but due to browser features like HSTS and HPKP (browser certificate verification), CWP page redirection may not occur. The following content will help you understand how NAC's blocking page operates.
Method of Displaying CWP Page to a PC Attempting HTTP Communication
This describes how Genian NAC displays the CWP page to a PC attempting HTTPS communication. You can understand the principle by which the Genian NAC CWP page is displayed when a blocked endpoint attempts communication via a web browser.
This method uses a packet interception technique.
A PC that does not comply with security policies has its ARP table spoofed. All communication is routed through the Network Sensor. When communicating with a web server, the Network Sensor communicates instead of the web server.
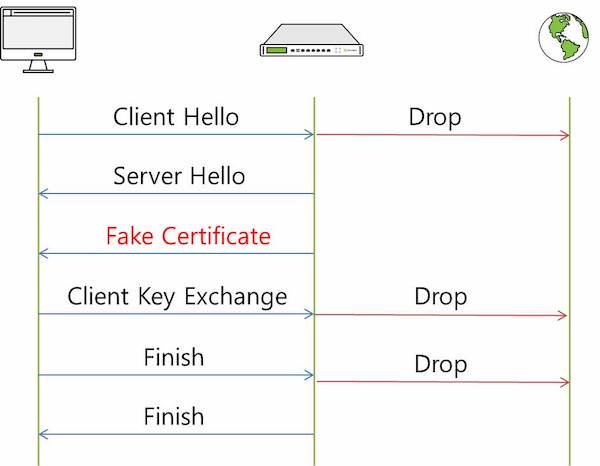
The important point here is that the server certificate is sent with a CA certificate generated by Genian NAC (a FAKE certificate), and an encrypted session is established with Genian NAC instead of connecting to the web server, allowing the Network Sensor to inspect the communication content. Therefore, Genian NAC can display the CWP screen on a PC that does not comply with security policies. However, when a user who has not complied with security policies accesses a specific website, the browser screen might only show "Your connection is not private" and the CWP screen is not displayed, due to HSTS and HPKP features.
1. CWP Page Not Displaying Due to HSTS/HPKP
Symptoms
When a user's PC not complying with security policies accesses a specific website, the browser screen displays the message "Your connection is not private. (IE: This site is not secure.)"
Cause
This section explains situations where Genian NAC fails to display the CWP page and how to control users who do not comply with security policies.
When a target PC attempts to access an HTTPS site, Genian NAC delivers its own certificate to the target PC instead of the specific site's certificate.
Here, the browser compares the PIN value of the certificate received from Genian NAC with the pre-registered PIN value of the specific site. If the PIN values are determined to be different, Genian NAC cannot establish an encrypted session between the controlled PC and the encryption target, and thus cannot display the CWP page to the user's PC.
Therefore, when accessing a specific site, the controlled user PC is not redirected to the CWP screen and only displays the message "Your connection is not private."
Note
What is HSTS (HTTP Strict Transport Security)?
- A setting that forces clients to request HTTP packets only as HTTPS.
- A setting that enforces HTTPS from the first request by inserting 'Strict-Transport-Security' into the web server's response header.
- Can prevent SSL Strip attacks, which are a form of Man-In-The-Middle (MITM) attacks.
What is HPKP (HTTP Public Key Pinning)?
- A setting that fixes (Pins) the certificate used for SSL/TLS encrypted communication between the client and server to the certificate of the final server.
- If a connection request is made with a certificate that has an incorrect PIN value, it compares with the pinned certificate and denies access if they differ.
- In other words, it can prevent Man-In-The-Middle (MITM) attacks.
Solution
This is an issue that occurs in all security solutions that use redirection features, and other countermeasures are currently being considered.
2. CWP Redirection Not Occurring When Using a Proxy Server
Note
From version 5.0.53 (LTS), CWP Redirection has been improved to work even when connecting via a Proxy. (#25704)
Symptoms
When a node assigned a policy that restricts network access attempts to connect to a web page, CWP page redirection does not occur.
Cause
This problem occurs because the endpoint's traffic passes through a Proxy server, which prevents proper redirection.
Solution
Add the Policy Server's IP as an exception in the Proxy settings.
Please refer to the section below for information on how to add exceptions.
.pac file modification example
function FindProxyForURL(url, host) { if (isInNet(host, "[Policy Server IP]","255.255.255.255"))
return "DIRECT"; else return "PROXY [Proxy Server Address]"; }
.dat file modification example
function FindProxyForURL(url, host)
{
if (isPlainHostName(host) ||
isInNet(host, "x.x.x.x", "255.255.255.255"))
return "DIRECT";
else
return "PROXY proxy.company.com:8080";
};