Integrating Seceon aiSIEM
This document describes how to integrate Seceon aiSIEM with Genian NAC using syslog. This integration provides the ability to extend Seceon aiSIEM threat detection capabilities into the Enforcement capabilities of Genians NAC. A full video Webinar covering this integration along with a demo is available on the Genians website under Resources > Videos.
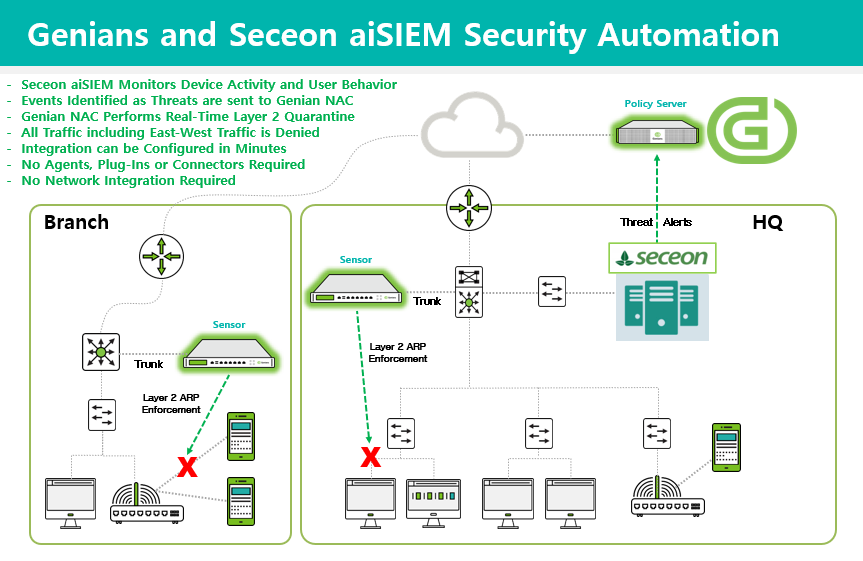
The main steps of this integration are as follows:
- Configure a Remediator in the Seceon APE
- Configure Genian NAC to interpret this syslog event sent by the APE Remediator and apply enforcement to the impacted node.
APE Remediator Configuration
Login to the Seceon APE UI:
- Under Administration > Remediator > Add, select Genians NAC as the Device, Firewall as the Device Type and enter the IP of your Genian NAC Policy Server.
- The User Name, Password and Confirm Password fields are mandatory but not required for the integration to function so can be populated with any data.
Genian NAC Syslog Configuration
A Server Rule set must be added before receiving syslogs. We will configure a server rule based on the format of the Seceon aiSIEM message to extract information about the device to be blocked. In this integration, we will use the IP address to identify the device to be blocked.
- Navigate to General > Log in the Preferences section.
- Click the Add button to the right of the Server Rules label, and fill out the pop-up form.
- Enter a name for the Rule.
- For Filter,select a variable by which to evaluate incoming syslogs for allowance. Choose from Program , Host, Match, or Netmask. This option allows for syslogs from a given source location/ program, or a given message content to be allowed. In this case, select Host.
- Define a Filter Value. If the Filter variable of the imported syslog matches the Filter Value , the syslog will be merged into the policy server logs. In this case, enter the Seceon CCE IP.
- Define
src_ip:as a prefix for IP values. - Define the character set which the syslogs will be imported in.
- Click Add at the bottom of the pop-up window.
- Click Update at the bottom of the Log Preferences page.
Now the message from the Infoblox system will be correlated with the nodes detected by Genian NAC.
Genian NAC Tag and Policy Configuration
Under Preferences > Properties > Tag:
- Create a tag called “Seceon-Threat-Detected” then click Save. This tag will be linked to a log filter and eventually to an Enforcement Policy in future steps.
- Click on Log and then Add filters. Syslog alerts from Seceon aiSIEM include the key words “THREAT so performing”. Type these words into the Description field of the log filter and click Search. You can further narrow the search by using the IP of your Seceon system.
- Give the log filter a name, description and add the previously created “Seceon-Threat-Detected” tag then click Save. In this example, we will apply the tag to the node (MAC+IP), though log filters can also apply tags to MACs, Users, or WLANs. Be sure to select Node in the From and To sections.
Under Policy > Group:
- Click Tasks > Create to create a new Node Group.
- Under General enter an ID and Description and set the Status to Enabled.
- Under Condition, click Add to add the previously created “Seceon-Threat-Detected” tag.
- Click Save.
Under Policy > Enforcement Policy:
- Click Tasks > Create to create a new Enforcement Policy.
- Follow the wizard and select the previously created “Seceon-Threat-Detected” Node Group.
- Select the desired Permissions, enable Captive Portal and enter a message to be displayed to the end user.
- Click Save.
With all configurations now in place, the Genians Network Sensor must be switched from Monitoring to Enforcement mode to facilitate the Layer 2 quarantine of non-compliant nodes on the network. Navigate to System > Sensor > Edit Sensor Settings and set the Sensor Operating Mode to Enforcement then click Update at the bottom of the page.
Testing and Validation
- Select a test machine within a network that is managed by a sensor from your Seceon Integrated Genian NAC system.
- Browse to a Seceon designated malware site with a test machine.
- In roughly 1-3 minutes (time required for Seceon threat processing), Seceon will send a syslog alert to Genian NAC.
- The test node should have Tag assigned once alert is received from Seceon.
- The node will then be Layer 2 quarantined in real-time by Genian NAC. Pings will fail and if any new websites are accessed, a captive portal will be display indicating the device has been quarantined due to a Seceon detected threat.