Integrating Cisco ASA - Applying Dynamic ACLs
If users are accessing your network using Cisco ASA (or a comparable solution) as a VPN gateway, you can use the Genians RADIUS Server to apply a dACL to perform role based access control to various network resources.
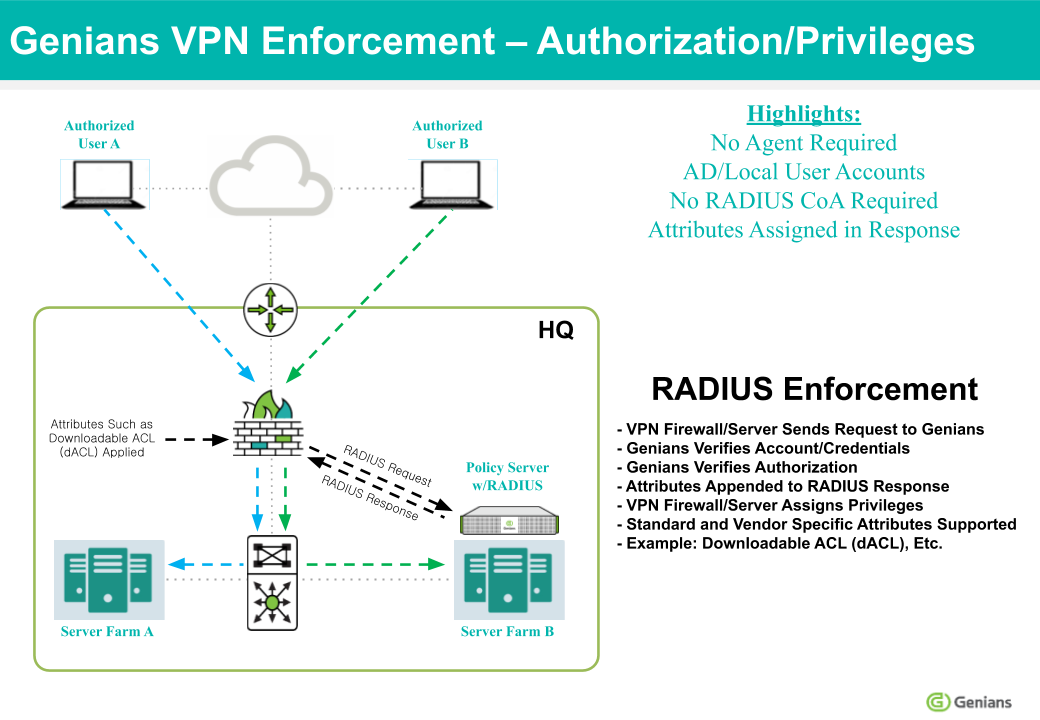
Integrating the Radius Server
First, ensure that the RADIUS Server is properly configured, and that your settings are compatible with your VPN environment.
See: Configuring RADIUS Enforcement
Next, configure Genian NAC as an Authentication Server in your VPN settings, by entering the Shared Secret, Server Address, Authentication Port, Accounting Port, and other info, as shown in the example below:
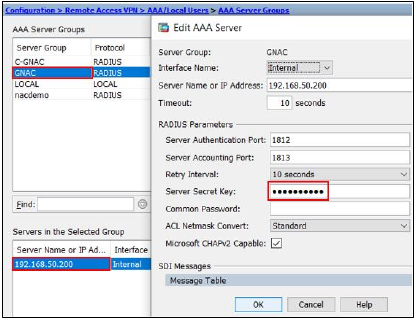
Configuring dACL
This can be accomplished by configuring an RADIUS Policy, and setting the Access Policy to ACCEPT, then setting Cisco InBound ACL for Additional Attributes.
In this example, we will use the User-Name attribute, and the Genians User Group feature to limit group members network access to a single server.
Go to Policy in the top panel.
Go to Policy > RADIUS Policy in the left panel.
Click Tasks > Create
For General, input Name, Priority, and activation Status.
For Conditions, select Attribute. For this example, select User-Name.
Set Operator and Value to user is one of the User Group and [Your User Group]
Click Add button.
For Policy, choose to ACCEPT Authentication Requests that match the attribute conditions, and select Cisco InBound ACL for Additional Attributes
For Value, enter a Cisco ACL, example:
Permit ip any host 192.168.55.200 deny ip any any
Click Add button.
Click Create button.
When an Authentication request is accepted from a member of the selected group, the access control list will be applied, thus limiting access to network resources.
For more info on on authorization through RADIUS Attributes, see: Configuring Authorization