Integrating FireEye
This guide provides an overview of integration with FireEye.
1. About this Guide
The guide describes how to integrate Genian NAC and FireEye.
When a specific anomaly is detected by FireEye, FireEye sends anomaly information detected to Genian NAC through SYSLOG Genian NAC will be able to prevent the spread of anomalies by quarantine the anomaly target.
2. Deployment of Genian NAC using FireEye
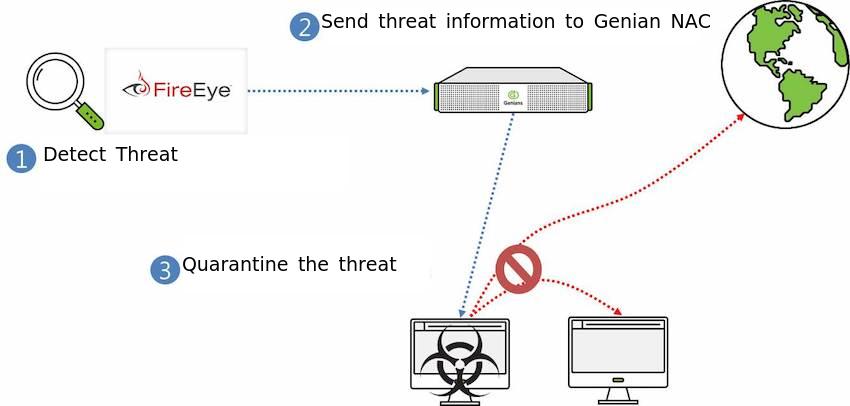
- FireEye detects the threatening device.
- FireEye sends the anomaly information to Genian NAC via SYSLOG.
- Genian NAC quarantines the device to prevent compromising other assets on the network. Other automated responses may also be configured.
3. Configuring FireEye for integration via SYSLOG
3.1 Configuration of Genian NAC
For Genian NAC to receive and use the information from FireEye, the internal
SYSLOG server must be configured to properly extract node information from the
incoming log. The Type and Type Value variables determine which
information sources will be accepted, and how they will be categorized. The
IP Prefix and MAC Prefix
- Login into Genian NAC with the administrator account
- Go to the Preferences tap on the top panel.
- Go to the General > Log on the left panel.
- Add the Filter in Server Rules in the middle of the center
- Enter the content
| Name | FireEye |
| Filter | host |
| Filter Value | [IP address of FireEye] |
| IP Prefix | src= |
| MAC Prefix | smac= |
- Click the Add button below and Update button
3.2 Configuration of FireEye
The FireEye appliances are very flexible regarding Notification output and support the following formats.
- CEF
- LEEF
- CSV
For our guide, we will use CEF Complete the following steps to send data to Genian NAC using CEF:
Log into the FireEye appliance with an administrator account
Go to the Settings tap on the top panel.
Go to the Notifications on the left panel
Click the rsyslog on the middle of the center
Check the “Event type” in the check box
Make sure Rsyslog settings are
Default format: CEF Default delivery: Per event Default send as: Alert
Add Rsyslog server on the middle of under > Enter the Name Genian NAC > Click on Add Rsyslog Server button
Enter the IP address of the Genian NAC in the IP Address field
Click the Update button below
3.3 Verification
- Go to Log on the top panel of Genian NAC.
- Messages from FireEye will show. The Sensor column data will show the IP of the FireEye system, and the Description column data will show a FireEye signature.
4. Apply Genian NAC Policy based on FireEye Data
Once Genian NAC is receiving SYSLOG data from FireEye, the device information contained in the log files can be used to automatically apply Tags to individual nodes. These tags can be used to group nodes for organizational, or policy purposes.
To apply policy through log tagging see: :Assigning Tags upon Log Occurrence